Continuous Ransomware Risk Assessment & Attack Surface Testing
Discover Riskiest Ports and Services Most Targeted by Ransomware Threats
Discover Riskiest Ports and Services Most Targeted by Ransomware Threats
Over 30% of reported cyber incidents in 2020 were attributable to ransomware and this may be underreported due to the stigma attached to reporting successful ransomware attacks.
Major Reasons for Increasing Ransomware Attacks:
At FireCompass we know that ransomware risk assessment is necessary if your organization is unable to answer questions like Recovery Readiness, Data and Operational Resilience, Business Impact, Defense Technology Readiness against real world attacks, and Ability to Detect and Respond to Phishing Attacks.
Gartner report shows that over 90% of ransomware attacks are preventable… security and risk management leaders can mitigate the risk..
No Software. No Hardware. No Additional Resources.
FireCompass helps your organization to evade ransomware that attacks risky ports and services such as FTP, RDP, and HTTP which account for about 50% of ransomware.
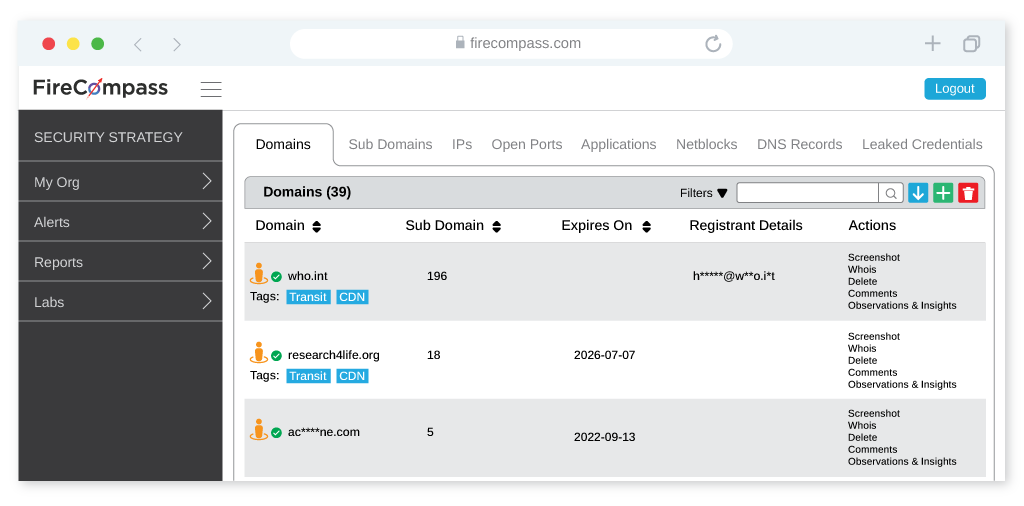
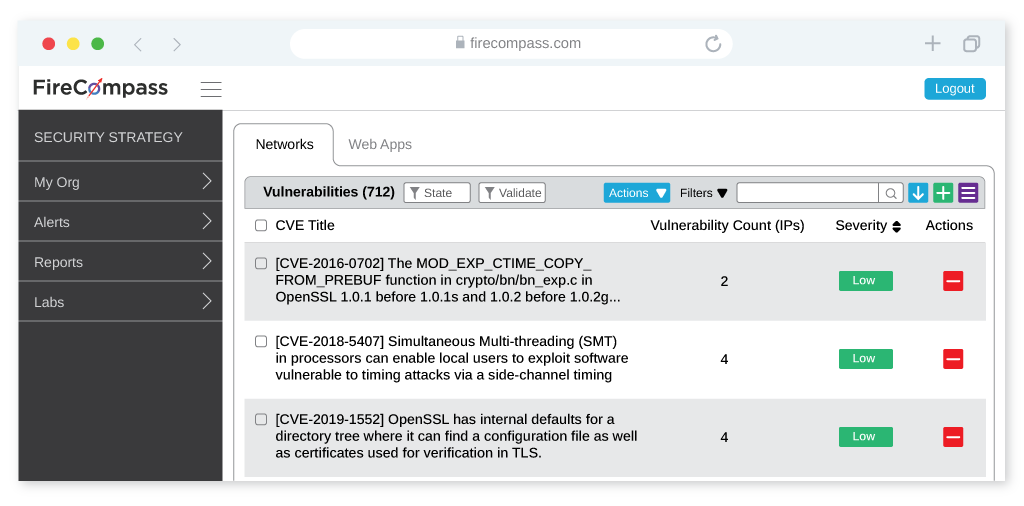
FireCompass helps organizations to reduce their Digital Attack Surface by identifying all unnecessary open ports/services & all possible vulnerabilities from Known and Unknown assets
FireCompass continuously analyzes the internet and provides alerts on any changes or risks associated with your digital footprint.
FireCompass runs continuously and indexes the deep, dark and surface web using the same reconnaissance techniques as nation-state actors. The platform automatically discovers an organization’s ever-changing digital attack surface, including exposed risky open ports like FTP, RDP, HTTP & more. For most ransomware attacks in 2020, RDP was the most common intrusion method used by threat actors.
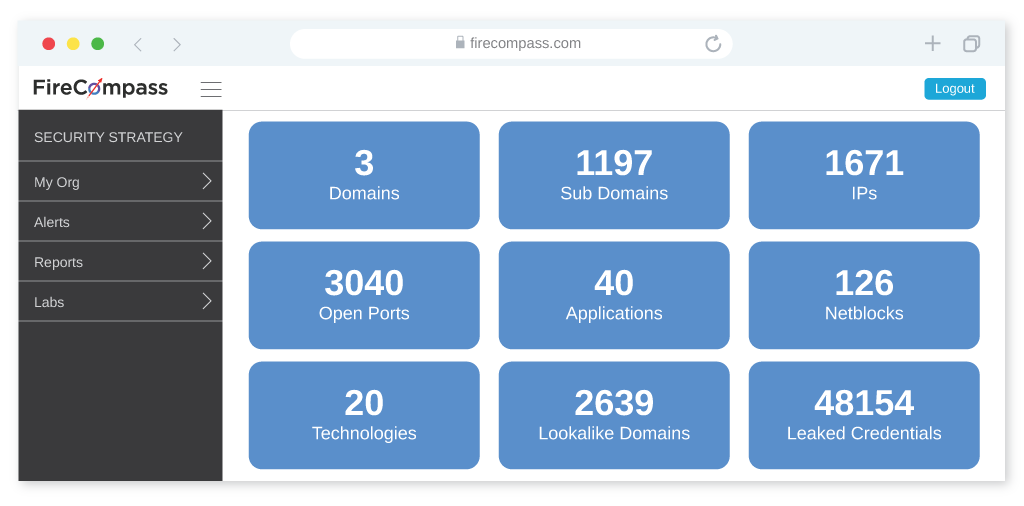
Reduce your digital attack surface with the Firecompass Platform by providing visibility into your web applications and cloud environments. It uses advanced scanning and monitoring to identify risks and vulnerabilities, and provides actionable recommendations to help you reduce your attack surface. Firecompass can also detect malicious activity and provide real-time threat intelligence to help you respond quickly to potential threats. Additionally, Firecompass provides automated compliance monitoring to ensure that your security posture meets the necessary standards.
FireCompass continuously analyzes the internet and provides alerts on any changes or risks associated with your digital footprint. This includes new ports, exposed RDP, risky assets, misconfigured databases, or any internet-facing infrastructure.
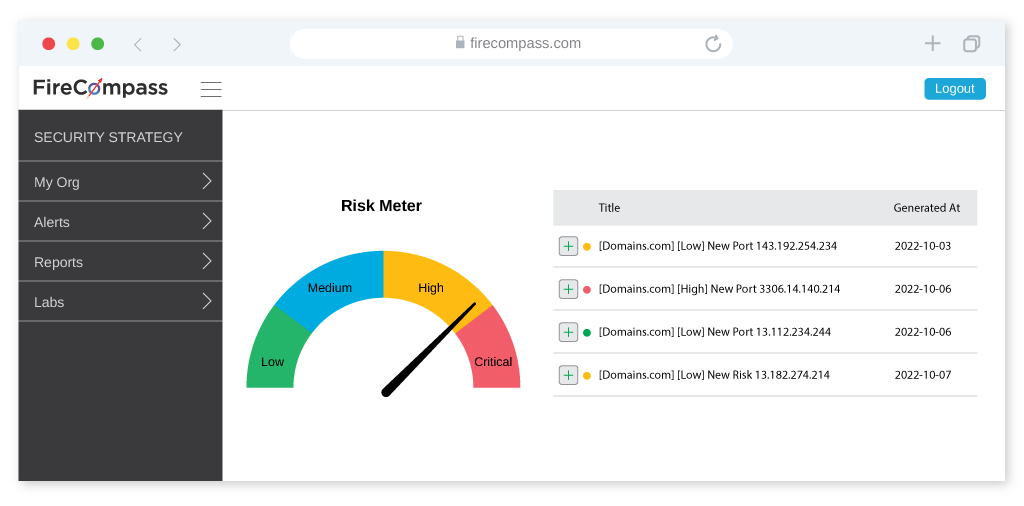
FireCompass helps to reduce attack surface by providing Digital Attack Surface Visibility & Mapping to help organizations remove assets which are not in use or not required.
The FireCompass platform identifies, analyses and prioritizes digital risks. The dashboard summarizes the high, medium, and low priority risks and recommends mitigation steps.
Continuously Test Your Entire Attack Surface and alert on any changes, including vulnerabilities, new ports or other changes to internet-facing infrastructure.

We’ve put together some top talks from global security conferences that could help you get a hang on the debatable topic

We have listed a few breach response tactics that organizations need to keep handy for rainy days. Read to know more about how you can keep your organization safe.

Here we list 10 tools which can be used for Reconnaissance by Security teams in order to assess their own security posture against hackers.
Note: We will provide an expert walkthrough of your findings using the FireCompass portal and followed by an Executive Summary report. We are providing free assessments to a limited number of organizations only.
Request Demo
You have successfully joined our subscriber list.
See your organization’s Risky Open Ports, Exploitable Vulnerability & Exposed Data that can be exploited by a Ransomware
©2024 FireCompass, All Rights Reserved.