Automated Pen Testing & Red Teaming across Web, API, Cloud & Infra.
FireCompass Agentic AI that Continuously maps Shadow Assets, Safely Validates Exploitability, maps Multi-Stage Attack Paths & Prioritizes Real Risks with Evidence-Backed results.
- Zero false positives
- 60X more ROI
- 90% reduction of risk window



Why Traditional Testing Fails - The 5 PAINS

Proofless Alerts
- 70%+ of alerts are false positives
- Lack of exploit path validation leads to noise
- No active testing to confirm real-world impact

Acute Talent Gap
- Offensive security experts are scarce, costly
- Manual pentesting doesn’t scale with asset sprawl
- High skill required to simulate real adversary behavior

Imbalance Gap
- Hackers exploit vulnerabilities in 3 days
- Lack of exploit path validation leads to noise
- Static assessments can’t keep up with dynamic threats

Narrow Scope
- Traditional Pen tests cover only 20% of assets
- Limited to known IPs and domains
- Misses shadow IT, pre-prod, orphaned or third-party assets

Siloed Testing
- 60%+ of breaches involve multi-stage attacks
- 90% of enterprises test in silos
- No chaining across apps, cloud, identity, and infra
Attackers are already ahead of you. They’re testing your defenses continuously, but you aren’t.
FireCompass Finds & Closes Every Gap Attackers Could Exploit
Agentic AI for Automated Pen Testing & Red Teaming
End-to-end automation with an expert in the loop
(Recon → PenTest → Red Team → PTaaS).
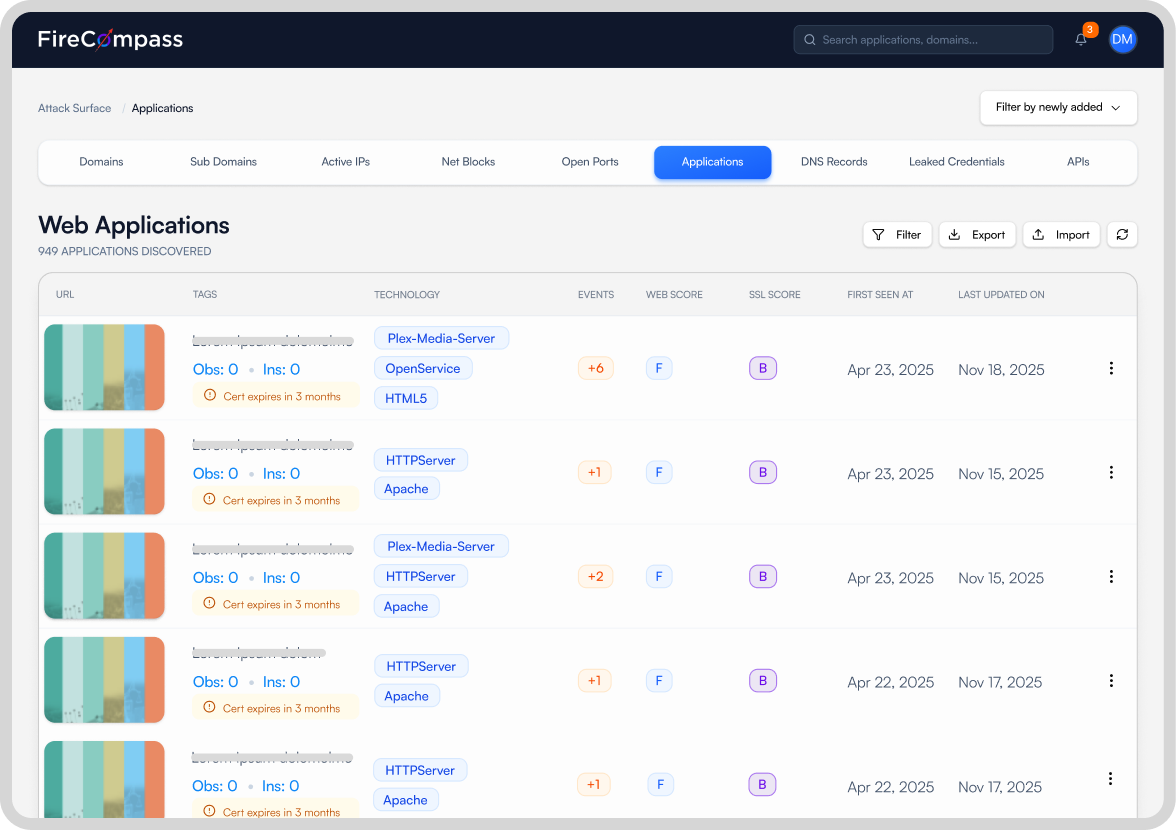
ASM + CTEM
- Automatically maps every attacker-visible asset using zero-knowledge recon
- Highlights crown-jewel paths and hacker targets using OSINT + active validation
- Daily delta reports, shadow IT discovery, leaked credentials, open ports, exposed cloud infra
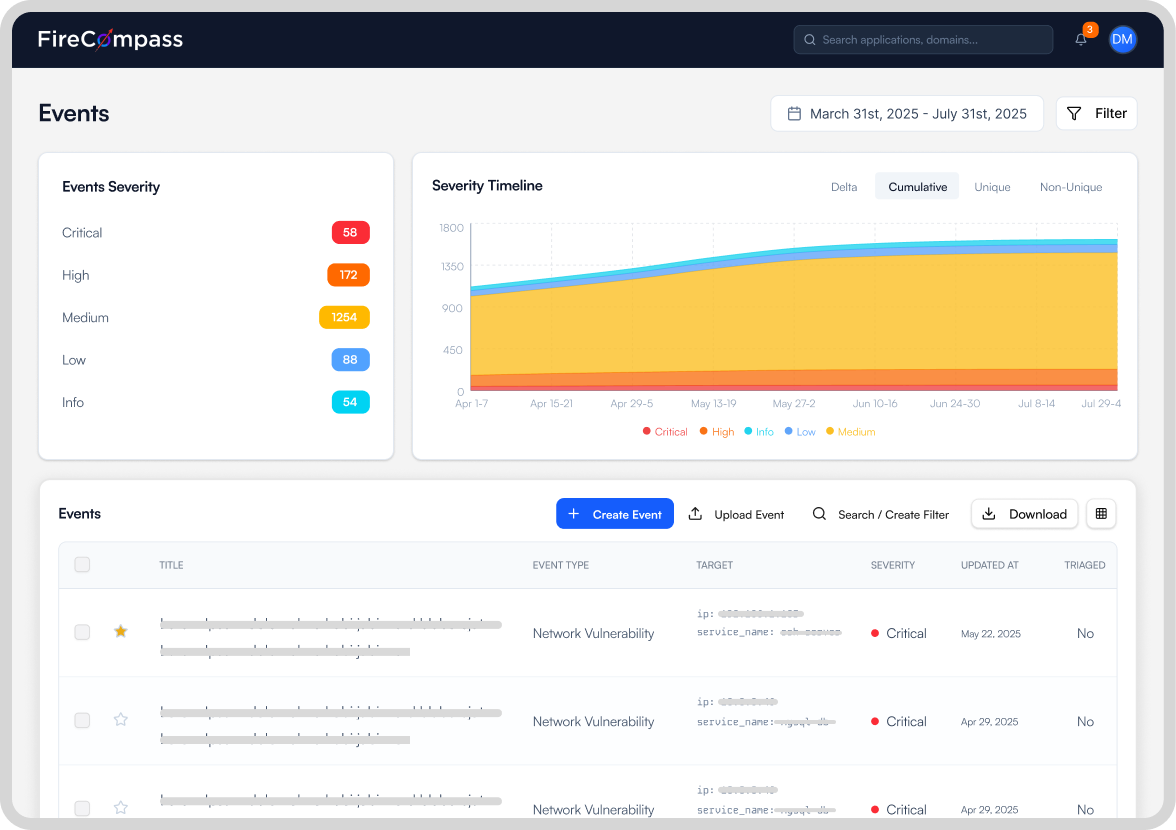
Automated Pentesting
- Network, web & API tests with proof-of-exploit
- Detects exposed admin panels, database ports, misconfigurations, and code flaws
- On-demand execution and continuous retesting with remediation guidance
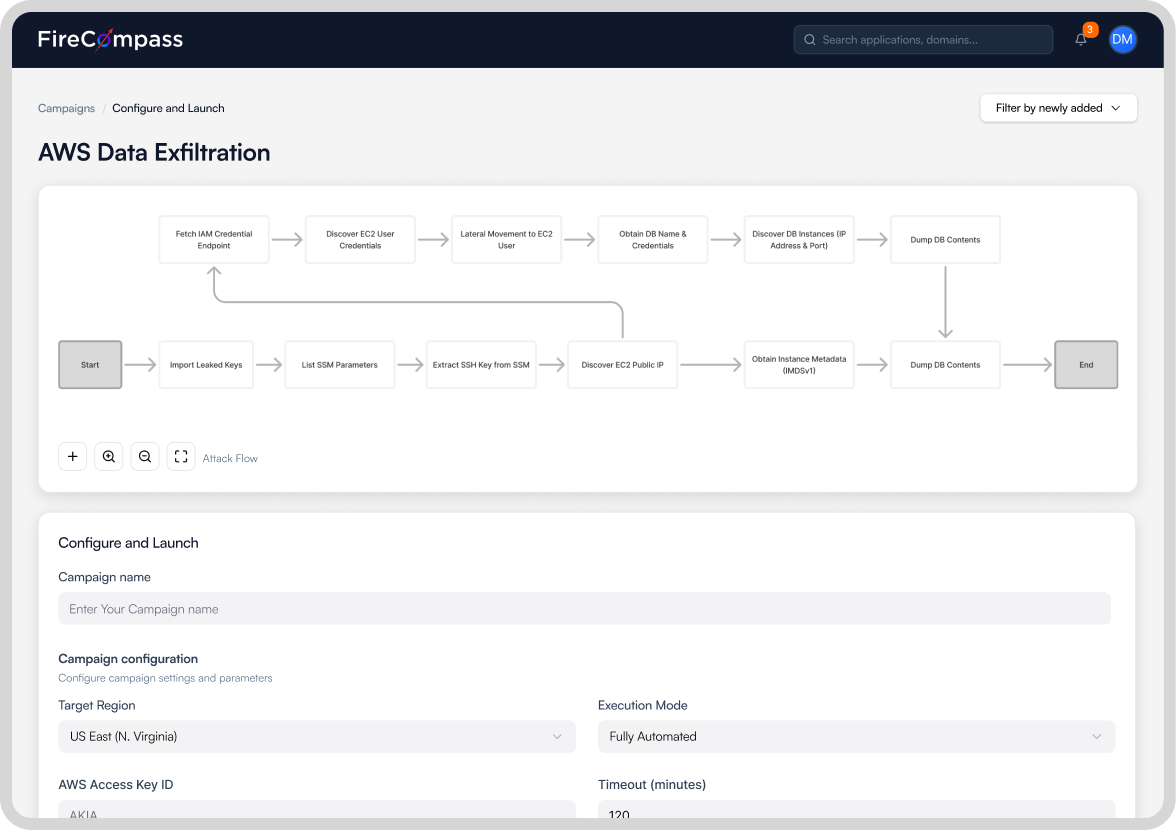
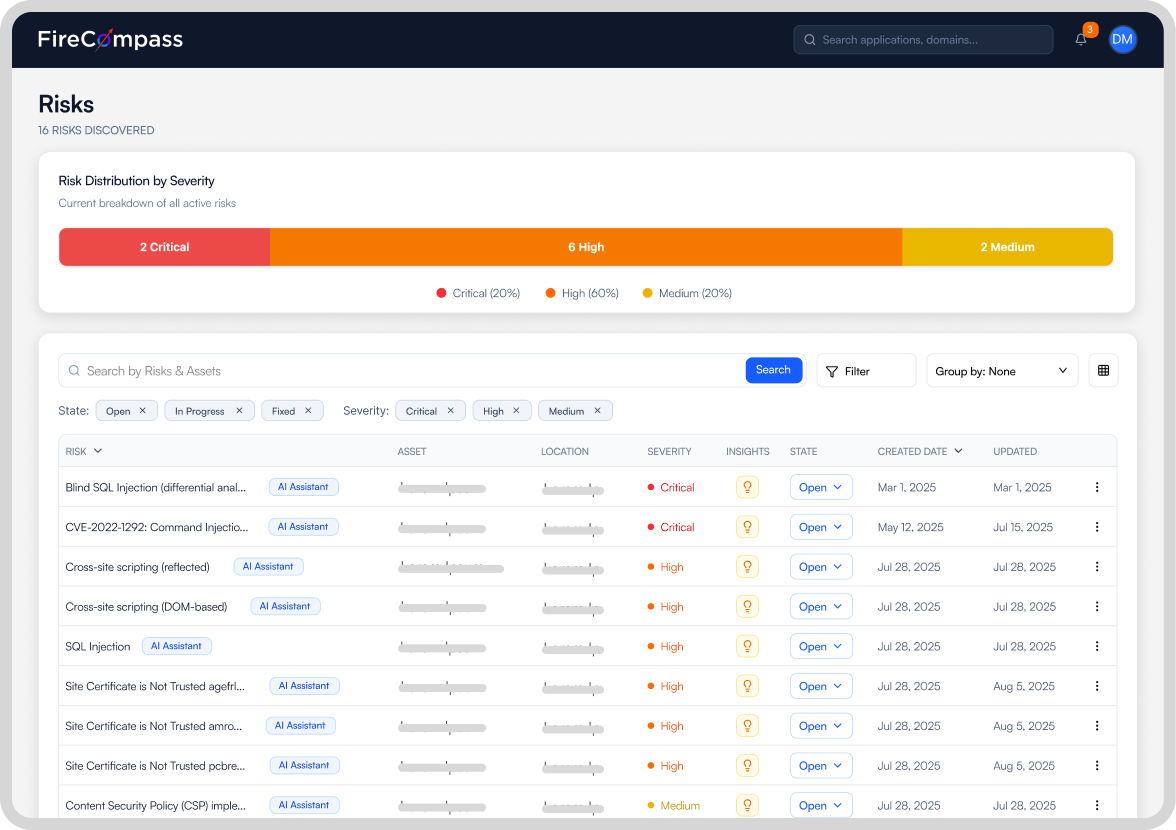
Continuous Red Teaming (CART)
- MITRE-aligned, multi-stage attack trees that emulate real-world adversaries
- Objective-based campaigns with credential-based lateral movement and privilege escalation
- Live attack path visualization, attack chaining, and custom playbooks
PTaaS
- Fully managed pen testing with expert-driven exploitation and business logic validation
- Compliance-ready reports, custom test cases, and on-demand requests
How Your Attack Surface Evolves With FireCompass
| Capability | FireCompass | Traditional Testing |
|---|---|---|
| Attack Surface Discovery |
|
|
| Attack and Exploitation Method |
|
|
| False Positives and NoisTesting Frequency |
|
|
| Risk window |
|
|
| Risk Prioritization |
|
|
| Testing Depth |
|
|
| False Positives Handling |
|
|
| Red Teaming Simulation |
|
|
| Business Logic Testing |
|
|
| Platform Model |
|
|
coverage
frequency
NAVIGATE Attacker Paths With Validated Proof : The 8 Advantages

Near-Zero False Positives

All-in-One Platform
7‑in‑1 platform that unifies Automated Red Teaming, Infra Penetration Testing, Application Penetration Testing, API Pen Testing, ASM, CTEM and PTaaS.

Validated Exploits
Instead of flagging vulnerabilities, FireCompass safely executes them to confirm exploitability to alert you about real vulnerabilities.

Intelligence: Live Attack Path Visualization
Shows end-to-end attack chains including lateral movement, privilege escalation, and data access.

Graph: Patented Attack-Tree Automation
Patented attack tree engine (PARC) chains multiple weak signals into real exploitable paths to prioritize true vulnerabilities

Agentic AI
Agentic AI – powered orchestration across asset discovery, attack simulation, and playbook generation.

Traversal & Lateral Movement Simulation
FireCompass simulates MITRE alligned full kill-chain behavior like credential reuse, session hijack, or domain hopping.

Expert-in-the-Loop
Business logic flaws and sensitive tests handled by FireCompass security experts embedded in the loop
60X More ROI Compared to Manual & Periodic Testing
Straightforward subscription, no hidden add-ons, no surprise invoices
Unlimited testing, retests, new assets, and new threats, all included

Single Platform. Multiple Use Cases
- Infrastructure Pen Testing
- Web & API Pen Testing
- Red Teaming / CART
- Attack Surface Management (ASM)
- Continuous Threat Exposure Management (CTEM)
- Zero-Day & N-Day Exposure Validation
- Penetration Testing as a Service (PTaaS)

FireCompass AI - Use Cases
- ASSIST - Highlight your specific attack-surface risks, answer “what/why/how,” and guide remediation.
- AUGMENT - Auto-create MITRE-aligned kill-chain plans, suggest attack trees and tests for your stack; configure/predict custom executions.
- AUTOMATE - Auto-generate test plans & execute safely; validate exploits; segment risks for small→large enterprises.

Trusted by Industry Leaders
Attackers Move Fast. FireCompass Moves Faster.
Continuous, AI-driven testing with human validation keeps your defenses ready every hour of every day
Working with the best
Forward Thinking Organizations Choose FireCompass for AI-enabled Pen Testing
“The tool has exceeded our expectations in identifying numerous domains and subdomains that are shown as public, but should be private.”
Risk Manager, Top 3 Telecom Company in USA
Build Your Security With The Best
FireCompass has built an AI-powered platform for Automated Pen Testing, Red Teaming & Attack Surface Management. We hold a USPTO-awarded patent for our Automated Red Teaming technology and trusted by top enterprises.
