Over the past decade or so, the frequency, as well as the volume of cyberattacks, has been growing at an exponential page. The largest companies of the world are being exposed to cyber attacks regularly, and even governments have not been spared, with national power grids bearing the brunt of cyberattacks from adversaries. There are various types of cyberattacks, and the type chosen generally depends on the security capabilities of the company being targeted.
There are various methods that can be used to stave off cyberattacks when they occur or to develop cybersecurity infrastructure that is robust enough to stop such attacks in their tracks. Two such methods are known as red teaming and blue teaming. Red teaming may be considered as a preventive method that works through a breach of your already existing cybersecurity systems. Red teaming has been growing in use over the past years due to its efficacy in exposing the cybersecurity loopholes in a system. On the other end of the spectrum is blue teaming. Blue teaming works much like traditional cybersecurity, in which all attempts are made to render your existing cybersecurity setup fool-proof and immune to outside attacks.
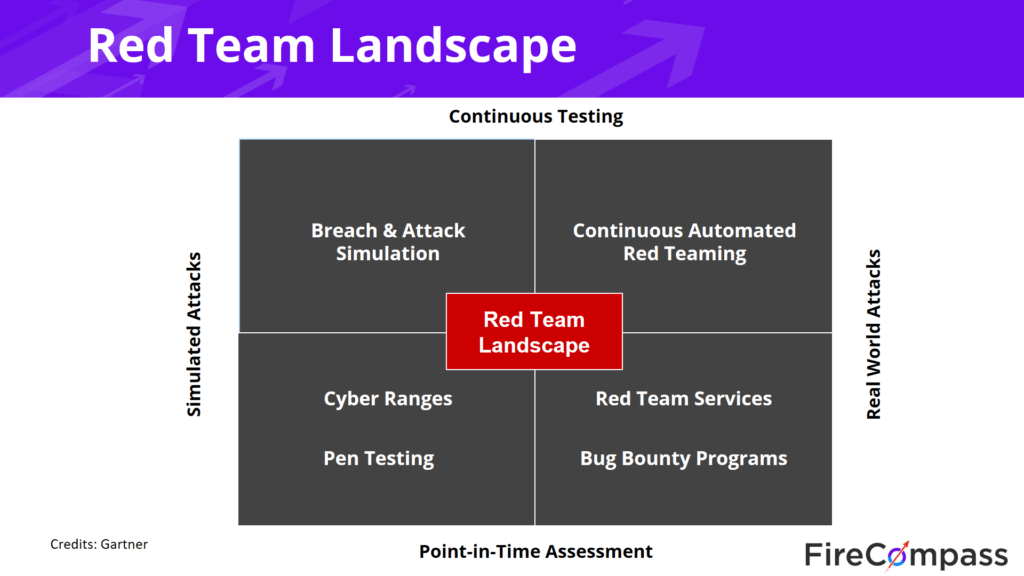
A red team is primarily a team of cybersecurity experts and professionals hired by a company to breach their cybersecurity systems and expose serious flaws and loopholes that can render their data unsafe. The key to red teaming is the anonymity of the process. While a company will generally have a contract with an external red teaming service, the red team will seldom inform the company when the cyber attack is going to be conducted. The victim is kept totally in the dark regarding the date and time of the attack and which specific part of the cybersecurity infrastructure will be attacked. After the attack, the red team will generally send in a report to the company regarding the perceived flaws in the infrastructure. While the role of a red team is offensive, that of a blue team is defensive. While a red team will carry out protracted attacks at a single point in time, the blue team must perpetually be on alert regarding the possibility of an attack from the red team. A blue team’s job is constant—to develop capabilities in the infrastructure to help detect attacks and protect data from them.
According to a study by Exabeam, more than a third of the organizations that used both blue teaming and red teaming observed that their blue teams could not detect attacks from red teams. Around 70% of all companies agreed that red teams’ exercises were more effective than those by blue teams. Around 72% of companies perform red team exercises with some regularity, and around one in four conduct such exercises on a monthly basis. More than 70% of all companies had been able to improve their security infrastructure and cybersecurity capabilities due to red team and blue team attacks, and for around one in five, this had had an impact on their bottom line as well
Continuous Automated Red Teaming
The level of sophistication among cyber attackers has been increasing significantly over the years. Nations have been using cyberattacks as a tactic of offense for some time now, and such actors have unlimited resources to focus on developing systems that can determine all the flaws in a company’s cybersecurity infrastructure. They can afford to continuously attack the security systems of a company until they find one small hidden loophole that they can later exploit. This is what the advantage of criminal actors such as attackers is as well. While companies will generally focus only on some of the sections of their cybersecurity infrastructure intermittently, cyber attackers are continuously attacking all of the systems of this infrastructure.
The answer to this problem is what is known as continuous automated red teaming. This is not a physical team of people looking to attack the security infrastructure of a firm, but rather a system set up by such people that persistently attacks all the parts of this infrastructure. Continuous red teaming aids you in always being alert and on the watch out for the next attack. Automated red teaming ensures that there is no dearth of resources when it comes to carrying out cyberattacks, which can be the case if humans are looking to attack each part of the infrastructure individually.
A continuous automated red teaming system will persistently assess all the cybersecurity levels that you have put in place. It will attempt to employ multiple methods to penetrate each level of your cybersecurity infrastructure, and once it has found an attack surface, will carry out a protracted attack to make its way to your data. Continuous automated red teaming is a modern method that ensures complete and total security and is generally more up-to-date than human red teams. The largest companies in the world that store heaps of user data have to ensure that their data is secure under all conditions and hence use continuous automated red teaming to root out loopholes in security.
Levels Of Red Team Adversaries
Not every attacker has the same level of sophistication and resources to conduct cyber attacks. There are several different levels of attacks, and firms need to be on the lookout for all such adversaries.
- Low-Level Adversaries: Low-level adversaries are generally individual cybercriminals or small groups of them that generally use tools bought off the shelf to exploit vulnerabilities in your system that are already known. These attackers are the largest in number and, as a group, the most persistent. Some firms can face such attacks on a nearly daily basis, but these attacks are easy to stave off since they are not the most sophisticated or novel in terms of technique. Small-level attackers can also be hard to identify due to their sheer number and are generally ignored when reporting.
- Advanced Adversaries: These adversaries are large attacker groups that use customized tools that are significantly more sophisticated. They will generally use novel ways to attack your systems and be more underhanded in their approach. Such groups are not associated with large organizations, but their hacking capabilities are compounded by the number of people in the group. These groups are fewer in number and easier to report and attack various different companies persistently, generally in order to procure and sell data or hold systems ransom for long time periods.
- Nation-State Adversaries: Nation-states use hacking as a tool of offense and can be associated with attacker groups that use the resources offered by governments to attack or disrupt a cybersecurity system. These adversaries are capable of evading most regular protocols that companies set up, and a firm expecting an attack from such adversaries must have multiple customized and robust security levels. Continuous red teaming helps protect from nation-state adversaries by exploiting all the vulnerabilities of the system and aiding your cybersecurity team in addressing them.
Benefits of Red Teaming
Several different benefits of red teaming have been laid out above. However, the reason why red teaming is used is that it has several benefits outside of being able to root security vulnerabilities. Let’s have a look at all the benefits of red teaming.
- Training: Red teaming is probably the best training tool you can get for any employee of your company or any member of your cybersecurity team. For a novice, red teaming is the best method to determine which security vulnerabilities can be exploited by attackers. Beginner programmers and ethical hackers get to learn various different methods of penetrating systems, as well as tips and tricks that allow the most experienced cyber attackers to do so without being detected. Members of red teams get to learn from the best professionals in the business and absorb their experience. This way, when a real attack happens, these members are ready to play the role of a really capable defense.
- Metrics: Red teaming allows first to assess the performance of their security team. Without using a technique such as red teaming, it can be hard to know whether your security infrastructure is really fool-proof or not without there being a real incident that exposes these flaws. Through red teaming, you can determine how well your security team is doing and make recommendations for performance improvement. The reports generated by the red team also allows the team to understand which areas they specifically need to focus on.
- Awareness: Red teaming is the best tool to spread awareness about the importance of security in your firm. Additionally, it allows members of your security team to understand the types of methods that real attackers might use in their endeavor to gain access to confidential data your company hosts. In fact, not just your security team but also other components of your overall security, from guards to receptionists, are made aware of being alert of malevolent elements that might physically try to compromise your data.
- Qualification: Red teaming is perhaps the greatest tool if you want to test the qualifications of candidates for your security team. Increasingly, companies are looking to disregard the educational qualifications of candidates while looking for members in their security team. With the rise of amateur and freelance ethical hackers, companies now accord a much greater weightage to the skills that candidates possess during the hiring process. Among the multiple technical rounds can be a red teaming round, in which the knowledge of candidates of various intrusion systems is tested, and the capability of the candidate to stave off such attacks is assessed.
- Security: The most obvious advantage of red teaming is that it helps you improve your security infrastructure. However, it is often hard to improve one’s security capabilities without knowledge of what the vulnerabilities are. The blue team can be used to check vulnerabilities from a defensive standpoint and without necessarily attacking the system, but the benefits of this approach are very limited. Instead, a red team can be used to lead attacks on your system and check individual departments for vulnerabilities. Modern approaches such as continuous automated red teaming can be utilized to recognize every loophole in security infrastructure and conduct a complete overhaul of a company’s security systems. Various red teaming tools are available to third-party companies that provide security services. These tools must be utilized effectively to create a fool-proof security system.
- Updates: Red teaming isn’t just useful in exposing small vulnerabilities in your security apparatus. It can be really beneficial if you are looking to determine to what extent your security systems need to be updated to be truly secure. Not updating your security systems can be an issue in an era where even individuals are becoming more and more sophisticated. Red teams generally use the most modern methods to penetrate your system, allowing you some insight into whether your security apparatus is capable of withstanding such attacks or not. You can then proceed to update your security apparatus with the latest technologies in the cybersecurity domain.
- Compliance: In the past years, regulatory compliance requirements have been updated regularly with information concerning the cybersecurity domain. Companies of nearly all fields are now required to comply with some mind of cybersecurity regulation. Especially if you are looking to deal with the government or already hold government contracts, regulatory compliance in the cybersecurity field is a mandatory requirement. Red teams allow you to understand the types of vulnerabilities that exist in your security apparatus and to take steps to ensure that it complies with government standards. You can also have red teams target the specific part of your security apparatus that needs to comply with regulations.
- Justification of budgeting: Having a really robust security apparatus has become a must in today’s age. However, building such an apparatus can also be costly and impact the bottom line of your company. For a security manager, it can be hard to justify this cost if the company database hasn’t been breached seriously in a long time. Moreover, the senior management of the firm might consider expenditure on security an additional cost rather than a mandatory operational cost. To exhibit how a serious cyber attack can hard your company and its data, a red team attack can be really useful.
The Steps Of The Conventional Red Teaming Process

The following are the main steps followed in carrying out a red team attack.
- Reconnaissance: The first step in red teaming is to conduct research on the target company. Try and understand the security features that it advertises and collect information about the vulnerabilities of these systems.
- Weaponization: Once you have figured out what the vulnerabilities of a system are, work on determining the red teaming tools that you require to breach these systems. The capabilities of the resources and code that you use in breaching an organization’s systems determine your attack’s strength.
- Delivery: This is the stage when the attack really starts. You can use known vulnerabilities to gain control of the network or even use tactics such as accessing weak employee passwords through brute force. This allows you to gain a stranglehold over the employee’s network.
- Exploitation: Once you are in the system of your company and able to access data, it is your duty as a red team to demonstrate the level of access that you can gain into the client’s systems. When engaging with the client, you are sure to have agreed upon certain objectives of the attack. This is the time when you fulfill those objectives after entering the network of the client. You could indulge in command and control, data infiltration, privilege escalation, and a host of other activities to demonstrate the weakness of the cybersecurity apparatus of the client.
- Report: This is the final step of the red team engagement. After you have entered and exited the client’s network, you must report to them the vulnerabilities you were able to find in their network. The company will generally ask for a really detailed report that includes not just the vulnerabilities that were exploited but also recommendations on how to address them.
Conclusion
Red teaming is one of the best cybersecurity methods to determine the vulnerabilities in your security infrastructure and address them. Whether it is conventional red teaming or continuous automated red teaming, using this method can make your data immune to breach or penetration. For companies involved in high-security fields, red teaming is a must to ensure a robust security apparatus.
If you are interested in taking one step ahead and getting your company a robust continuous automated red teaming service, contact FireCompass for more information.




![[Upcoming Webinar]Future of Offensive Attack Simulation& CART (Continuous Automated Red Teaming) fi-1-11](https://firecompass.com/wp-content/uploads/2020/10/fi-1-11-300x200.webp)