Outpace Attackers
with Continuous
Penetration Testing
Single Platform for AI-Powered Continuous Automated Red Teaming (CART), Pen Testing & NextGen Attack Surface Management



Why Traditional Pen Testing Fails?
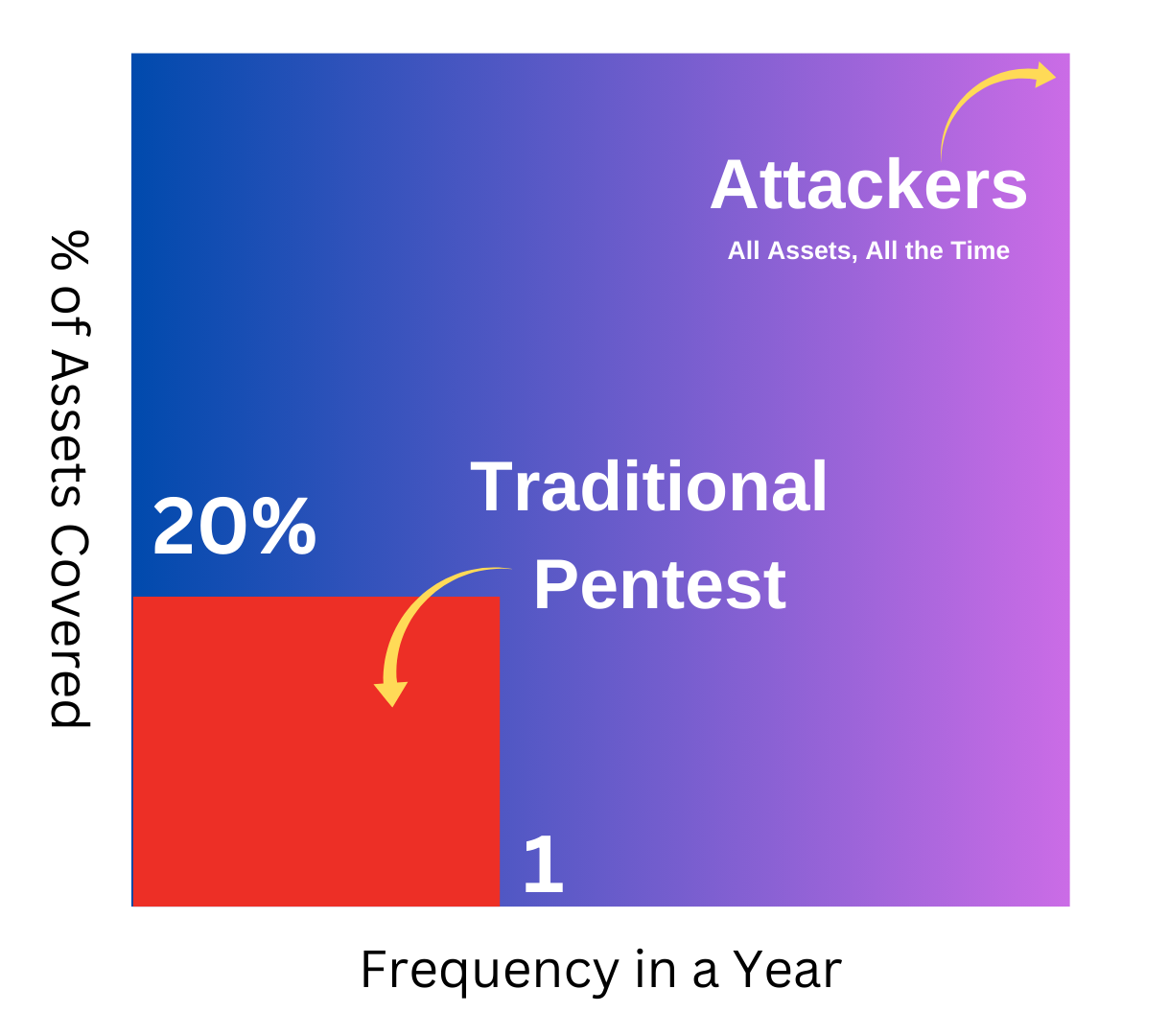
Organizations typically secure their most important assets, but fail to test pre-prod assets that often have production data. Hackers know this, and keep checking your peripheral assets for vulnerabilities.
Hackers exploit new vulnerabilities within 24 hours to 12 days, while companies take up to 30 days to discover, verify, prioritize and patch vulnerabilities. This leaves a big window of opportunity for hackers.
Fragmented tools, false-positive alert fatigue, expensive consultants and small teams mean the good guys are stretched. Even today pen-testing is largely manual, costly & time consuming.
AI-Powered Penetration Testing
Single Platform for Automated Pen Testing, Red Teaming & NextGen Attack Surface Management
Continuous Penetration Testing
Automate Network & Application pentesting beyond OWASP Top 10 to address a broad range of issues.
Continuous Automated Red Teaming (CART)
Continuous identification of vulnerabilities by emulating multi-stage cyber-attacks to pinpoint prioritized risks.
NextGen Attack Surface Management
Discover all assets, known and unknown, cloud asset or on-premise asset, to make sure nothing is overlooked.
AI-Powered Penetration Testing
Hack Yourself Before Others Do!
Continuously monitor
Discover Unknown
Risky Assets & Fix Critical Gaps First
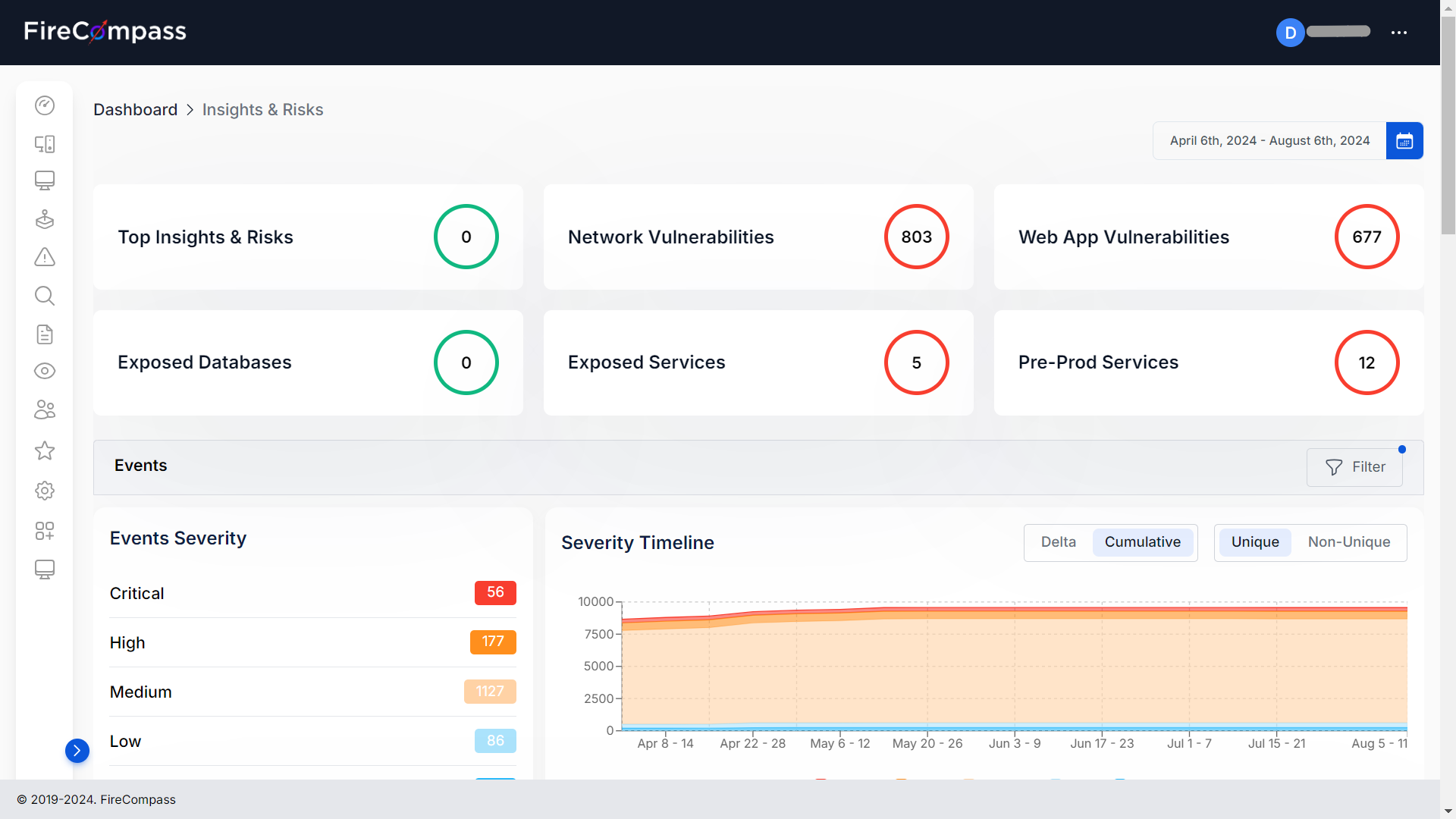
Continuously monitor and discover your entire attack surface with Passive & Active Recon, and be alerted of IPs as soon as they are exposed. Prioritize your vulnerabilities and reduce false positives by 99% so that you can focus on the most critical security gaps.
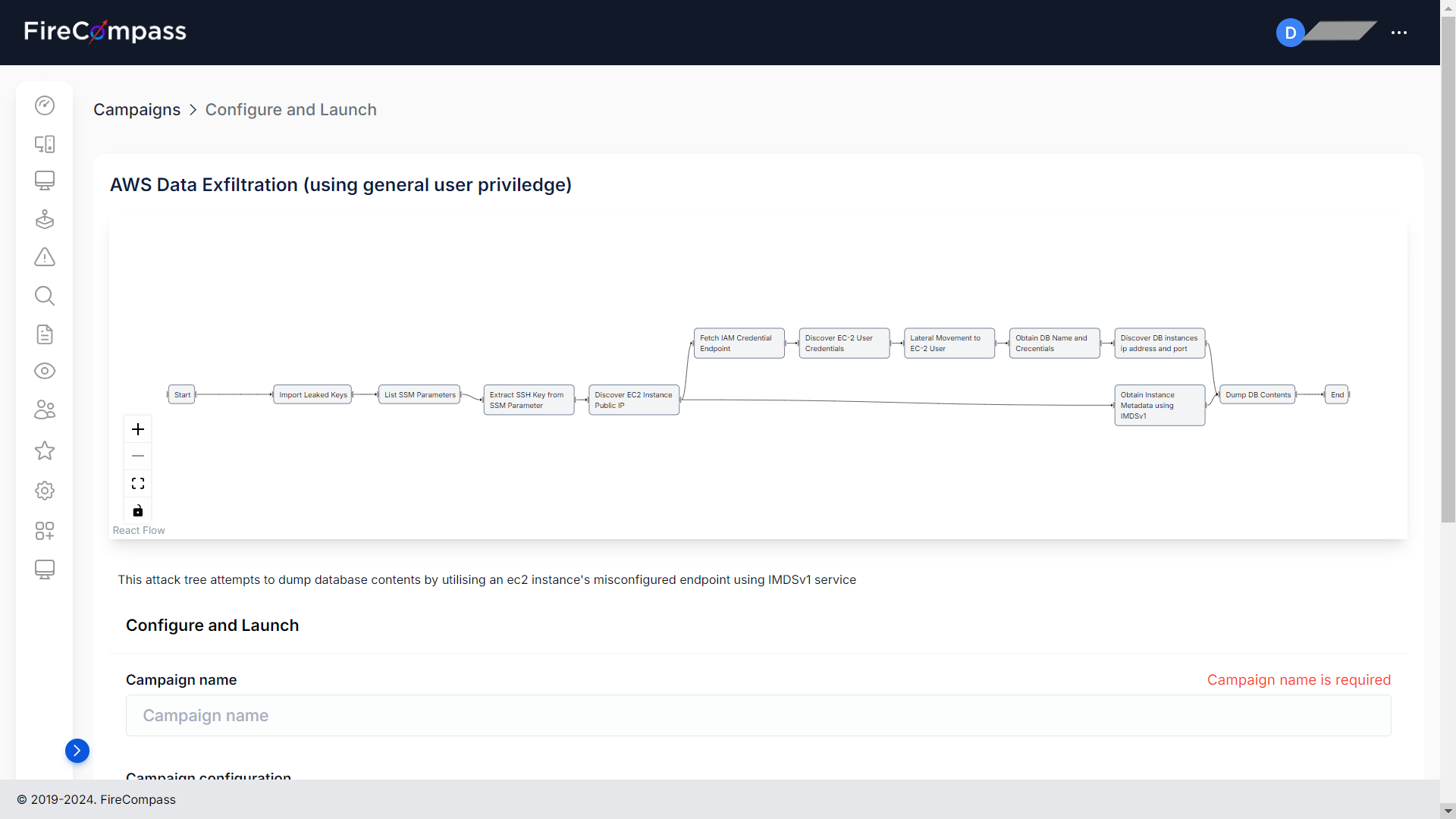
Automates complex paths
Run Multi-Stage Attacks With MITRE-Based Full Kill Chain Automation
FireCompass automates complex attack paths at scale with AI. What would take a team of pen testers days to do for a few assets, is done by FireCompass in seconds for a large number of assets.
Test your vulnerabilities
Test Your Defenses Vs Latest TTPs & Attacks
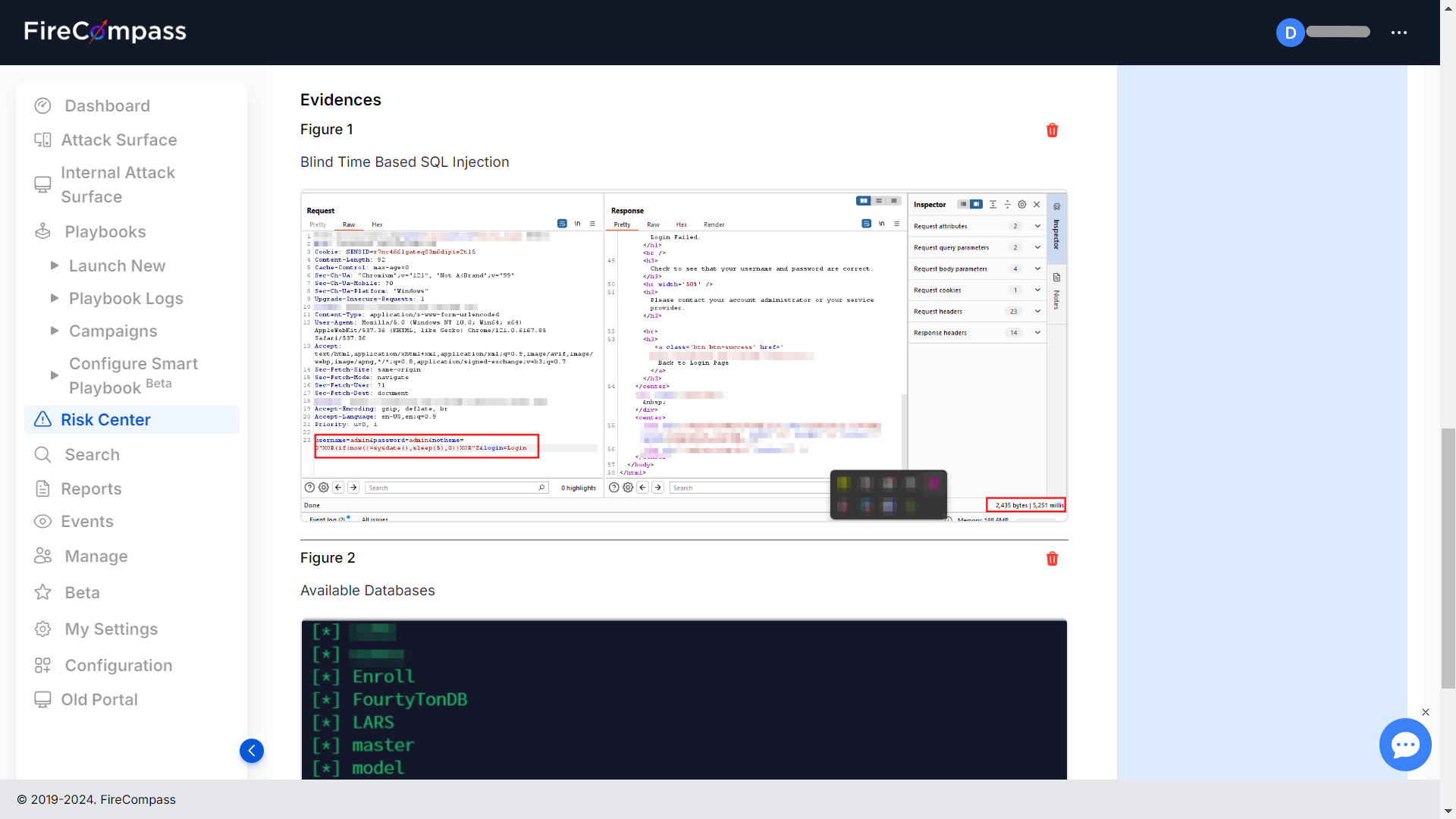
Run real-life attacks using TTPs (including specific CVEs, recon techniques, malware attack vectors, attack techniques). Test your defenses to check if they can defend against todays latest threats like Log4j, LockBit, CISA Alerts, nation threat actors & more.

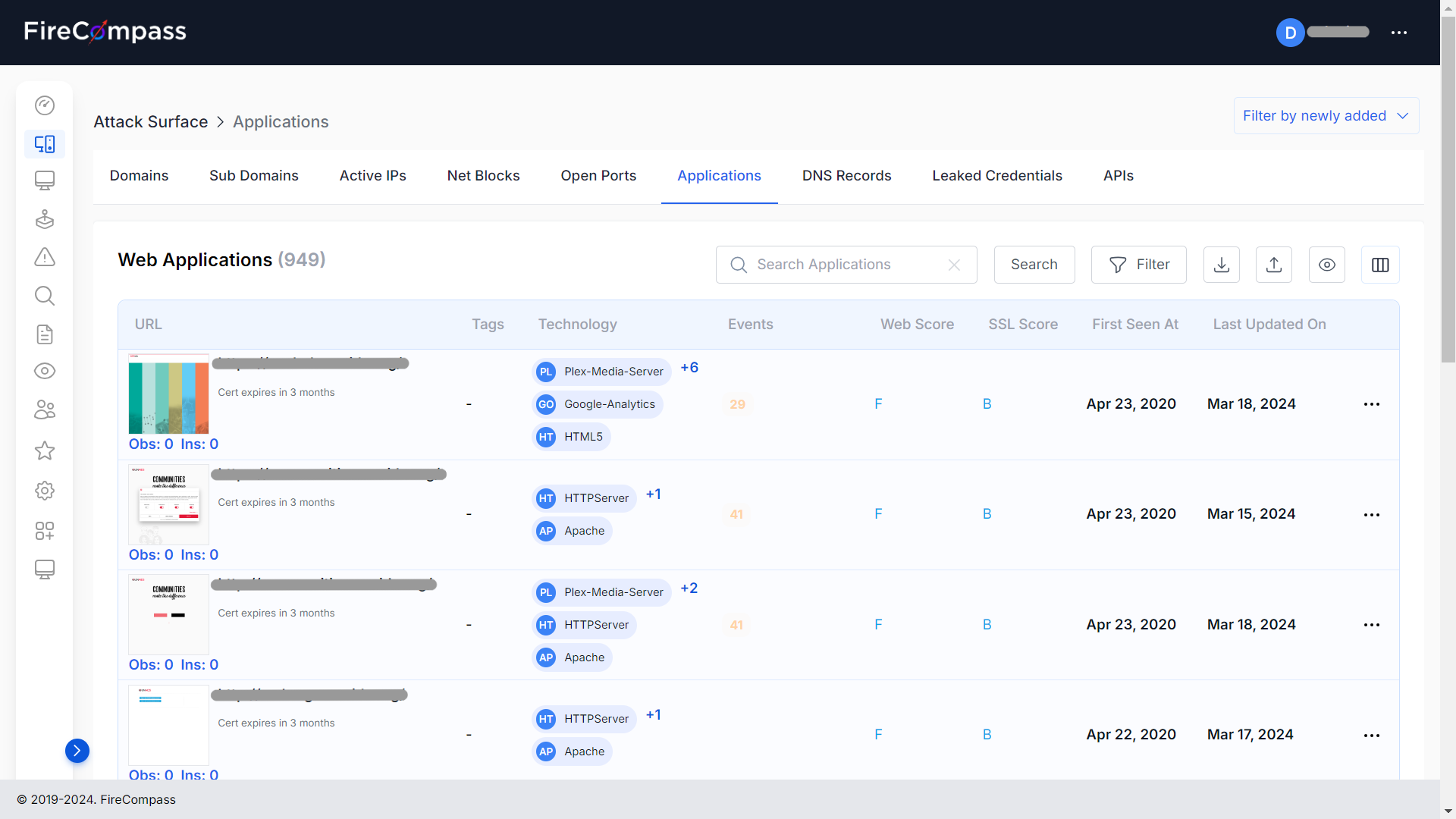
Pen Test As a Service
Pen Test As A Service (PTaaS) To Reduce Complexity
Use FireCompass’s AI enabled platform and Managed Services to receive an end-to-end Pen Test As a Service (PTaaS).
Passive Recon with Active Testing
Prioritized Alerts With No False Positives
FireCompass combines Passive Recon with Active Testing to validate & prioritize real risks. PTaaS combines humans and Automation to ensure that you have no false positives.
Featured In 30+ Analyst Reports
Standout Feature Is Its Autonomous Penetration Testing Suite
“FireCompass’s strengths lie in its comprehensive asset discovery and flexible approach to vulnerability assessment. Its asset categorization is notably broad and detailed, enhancing asset management capabilities. The platform’s standout feature is its autonomous penetration testing suite.”
Indexes The Web With An Always On Method Of Looking For Attack Vectors
“FireCompass Scans & indexes the web as a hacker would with an always on method of looking for attack vectors. It then launches attacks with continuous automated red teaming to repeatedly test customer’s attack surfaces. It wants red teaming to be available to all enterprises consistently, not just large organizations.”

Finds Gaps & Operational Deficiencies Not Found By Other Tools
FireCompass recognized in Gartner® Hype Cycle™ for Automated Red Teaming, Continuous Pen Testing & Attack Surface Management “Frequent and consistent testing helps find and mitigate weaknesses, gaps and operational deficiencies not found by other tools, in addition to reducing downtime and loss of revenue.”
A Proven Leader: Featured In 30+ Analyst Reports
Working with the best
We Are Rated 5 ★ on Gartner Peer Insights

Real Time Rrioritized Risk Alerts & Monitoring
FireCompass is providing us exceptional services in external attack surface monitoring. They give us up to date real time prioritize risks alerts and monitoring. The tool also provides Red teaming and external attack surface evaluation with the current cyber security trends.
Real Time Rrioritized Risk Alerts & Monitoring
FireCompass is providing us exceptional services in external attack surface monitoring. They give us up to date real time prioritize risks alerts and monitoring. The tool also provides Red teaming and external attack surface evaluation with the current cyber security trends.
AI-Powered Penetration Testing
Working with the best
Forward Thinking Organizations Choose FireCompass for AI-enabled Pen Testing
“The tool has exceeded our expectations in identifying numerous domains and subdomains that are shown as public, but should be private.”
Risk Manager, Top 3 Telecom Company in USA
Build Your Security With The Best
FireCompass has built an AI-powered platform for Automated Pen Testing, Red Teaming & Attack Surface Management. We hold a USPTO-awarded patent for our Automated Red Teaming technology and trusted by top enterprises.

