“Implement CTEM and Reduce the Chance of Getting Breached by 3x” - Gartner
Organizations should implement Continuous Threat Exposure Management (CTEM) for three reasons:
- Continuous scanning and patching are unsustainable due to the effort required and diminishing returns.
- Attackers use automation to identify and exploit vulnerabilities, but traditional Vulnerability Assessment (VA) and Penetration Testing (PT) are disjointed and lack the agility to prevent attacks.
- While organizations focus on securing their most valuable assets, attackers often target peripheral assets, which make up 90% of the attack surface.
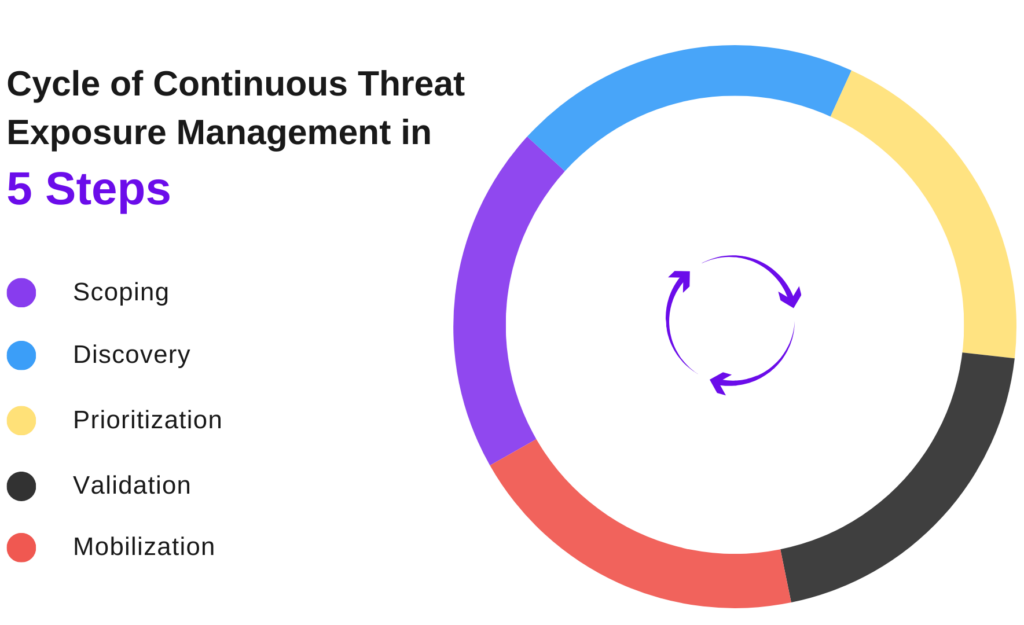
EASM+ Platform - Continuous Discovery, Active Validation & Continuous Risk Hunting
How FireCompass Helps
No Interruptions. No Deployment. No Hardware. No Agents.
Discover & Define Scope of Cybersecurity Exposure
FireCompass EASM aids organizations in uncovering their entire external attack surface, crucial for outlining their CTEM program's scope. By continuously sending probes, capturing banners, fingerprinting services, and attributing contextually, the FireCompass Recon Platform identifies assets associated with the organization. It organizes domains, subdomains, IP addresses, services, service banners, web application pages, and public code into a searchable, extensive graph of entities and their interrelations.
Pririoriize &
Validate Threats
The FireCompass platform assists organizations in uncovering both visible and hidden threats through playbooks designed to test various scenarios on your attack surface. It reveals hidden assets using advanced attribution techniques and employs Multi-Stage Hunting Playbooks to execute over 30,000 attacks and checks across network, web, cloud, and other assets via a geographically distributed sensor network. Additionally, the platform conducts continuous risk hunting with playbooks that identify critical risks within 24-72 hours and sends alerts.
Mobilze People and Processes
The FireCompass platform's Event Logs and Risk Center offer a continuous stream of threats and risks in one place. The platform facilitates collaboration among different teams by assisting in the prioritization and remediation of identified issues, mobilizing both people and processes effectively.
Discover & Define Scope of Cybersecurity Exposure
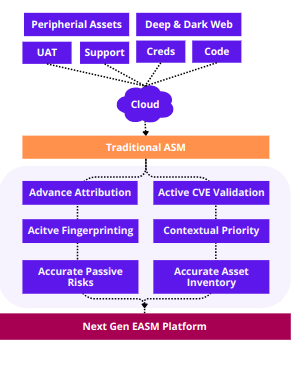
FireCompass EASM enables organizations to define the scope of assets based on business risks, discovering both visible and hidden assets. Scoping can be adjusted by including or excluding assets based on subsidiary levels, domains, tags, and other criteria. Once scoped, the FireCompass platform uses advanced attribution techniques on the deep, dark, and surface web to identify assets related to the organization. The attack surface management involves:
- Creating an inventory of assets for compliance and testing.
- Identifying and eliminating Shadow IT, such as public cloud buckets, exposed RDP, and other critical services.
- Identifying critical CVEs without active scanning.
- Understanding asset attribution details.
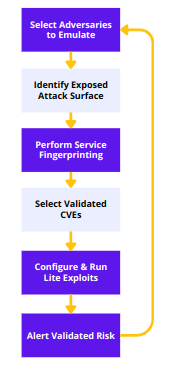
Prioritize & Validate Threats
CTEM propose to prioritize risks based on various factors such as urgency, availability of security controls and exploitability from attackers perspective. FireCompass Platform orchestrate various playbooks to identify critical vulnerabilities along with attack paths. It will also performs active validation of passive risks by performing active fingerprinting, probing and sending CVE specific payload. Active validation helps organizations to eliminate False Positives from Passive Risks. The platform performs further simulate Adversaries to identify low hanging attacker exposed assets
Firecompass Active Validation & Risk Hunting Platform helps organizations in various ways:
- Identify lesser secured and attacker targeted Peripheral Assets.
- Remove False Positive from Assets Inventory using advance attribution
- Actively ValidatePassive risks to reduce Passive Risks Alert Fatigue
- Prioritize Risks based on Attackers TTP
- Identify and Alerts Assets exposed to Day 1 CVEs
Mobilize People and Processes
Traditional Asset Inventory Solution, VM and Pentesting are disjoint exercises, handled by different tools and teams, and hence slow to respond. CTEM proposes to establish tools and process to reduce any obstacles to approvals, implementation processes or mitigation deployments.
The FireCompass platform’s Event Logs and Risk Center offer a continuous stream of threats and risks in one place. The platform facilitates collaboration among different teams by assisting in the prioritization and remediation of identified issues, mobilizing both people and processes effectively.
FireCompass Featured In Gartner® Hype Cycle For Automated Penetration Testing And
Red Teaming 2023
Benefits of Using FireCompass
5X
Assets Coverage
Conduct Pentest on 100% of Assets as compared to 20% of assets in traditional Pentest
10x Pen Testing Frequency
Scale your pentesting to monthly frequency as compared to yearly traditional pentest
50x Reduction of Risk Window
Identify most critical risks within 72 hours, and validate Security Controls at least monthly
80%
Cost Saving
Save upto 80% of your SecOps Bandwidth by Focusing on Prioritized Risks
Frequently Asked Questions
What are the benefits of Continuous Automated Pentesting with FireCompass?
FireCompass Continuous Automated Pentest enables enterprises to elevate their bi-annual Pentest exercises to a monthly frequency, while simultaneously ensuring 100% of assets are covered in each automated Pentest cycle. It offers 5x the benefits compared to employing additional resources for conducting traditional pen tests monthly. Additionally, the FireCompass Platform features a Continuous Threat Monitoring mode that identifies the most critical risks within 72 hours, significantly reducing the overall exposure window of a critical vulnerability.
What compliance standards are required in a Continuous Automated Pentesting?
- Continuous monitoring and penetration testing are beneficial for organizations regardless of their need to comply with regulations like GDPR, HIPAA, or PCI. These practices can help avoid the substantial penalties associated with breaches by enhancing security, even for entities not subject to specific compliance requirements. Continuous automated penetration testing, in particular, plays a crucial role in maintaining robust security measures.
How does an Automated Penetration Test differ from an Automated Vulnerability Scan?
An Automated Penetration Test attempts to exploit vulnerabilities to prioritize their remediation. In contrast, an Automated Vulnerability Scan merely identifies CVEs and vulnerabilities in an asset, assigning scores based on static CVSS metrics. An Automated Penetration Test also uncovers a series of attack steps, known as attack trees, which may involve CVEs, authentication attacks, web application vulnerabilities, process injection, lateral movements, etc. This approach helps to minimize noise and alert fatigue, and it uncovers new attack paths that vulnerability scanning might miss.
What should we expect from the FireCompass Continuous Automated Pentesting?
With FireCompass Continuous Automated Pentesting, organizations can expect thorough monthly automated penetration tests covering 100% of assets to identify vulnerabilities. It includes continuous daily monitoring for Critical Vulnerability Exposures (CVEs) with immediate alerts for critical threats. Additionally, users gain access to a comprehensive portal featuring detailed reports, a real-time dashboard, and over 100 tailored attack playbooks designed to address specific vulnerabilities on your attack surface, enhancing your cybersecurity posture significantly.
How often should we conduct an automated Continuous Automated Pentest?
FireCompass Automated Continuous Pentest is performed monthly on 100% of your assets to uncover recent and new exploitable vulnerabilities. Additionally, the platform features a continuous Day 1 CVE monitoring mode, which identifies and alerts you to newly published CVE exposures within 72 hours.
How much time is required to perform a typical Automated Pentest?
- An Automated Pentest typically requires 3 to 15 days to cover 100% of assets, encompassing different types of network and web assets, with the duration varying based on the size of the attack surface. The scheduling of tests is designed to minimize the impact on the performance of your services and web applications. In certain instances, Automated Pen tests may throttle testing to ensure the impact on your attack surface remains minimal.
I already have a vendor conducting yearly Pen Testing, do I need a Continuous Pen Testing solution?
Are you struggling with Alert Fatigue from Scanners or threat intel feeds?
Is your pentest vendor able to cover 100% of assets? As per our research, a typical pentest just covers 20% of assets
Are you worried about breaches and ransomware in your industry?
Is your industry highly regulated and compliance-driven? There can be hefty fines in case of non-compliance
Then Continuous Automated Pentesting can help your organization to cover all the above concerns, and improve the overall security posture of your organization.
Important Resources

We’ve put together some top talks from global security conferences that could help you get a hang on the debatable topic

We have listed a few breach response tactics that organizations need to keep handy for rainy days. Read to know more about how you can keep your organization safe.
Read More

Here we list 10 tools which can be used for Reconnaissance by Security teams in order to assess their own security posture against hackers.
About FireCompass
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM) that acts as an integral part of a good exposure management program.
- Single Platform for Attack Surface Management and Automated Penetration Testing & Red Team
- Daily Risk Port Scanning & Adversary Emulation through multiple Attack Playbooks
- Prioritized Risks with real-time alerts for faster detection and remediation
Request Demo
Thank you!
You have successfully joined our subscriber list.
