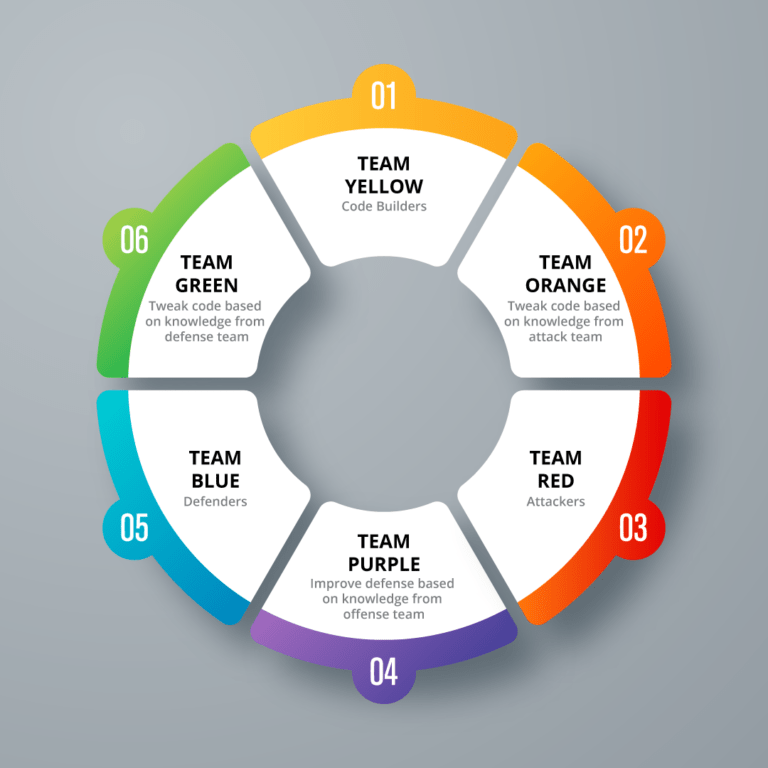
Like any other field of work, Information Security requires teamwork for the success of its objectives. Each team has varied skills and roles that contribute to the whole objective of protecting essential information from unauthorized access. Traditionally, there have been two primary teams in information security: red and blue teams. In 2017, April C. Wright wrote a paper that advocated for the Information Security color wheel – which is an expansion of the Information security working group to include more teams such as yellow, green, purple, orange, and white teams working alongside the primary red and blue teams.
The InfoSec Color Wheel
The InfoSec color wheel calls for collaboration between software development and information security teams. The overall objective of the InfoSec color wheel is to have a bridge between development and security. With this collaboration, developed products come with enhanced inbuilt protective measures against unauthorized intrusion.
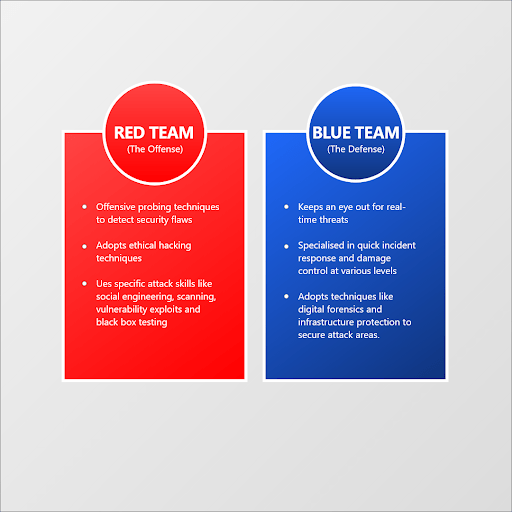
So what is the difference between the red team and the blue team?
Let’s learn more about the key differences between red team vs blue team in the field of cybersecurity. Red and blue teams play a primary role in protecting an organization’s sensitive data and systems from cyber-attacks. A blue team is simply a “defender” of an organization’s network, while a red team is an “attacker” of the same network. The blue team erects defensive mechanisms against intrusion, while the red team tries to break into the mechanisms. Red team and blue team security work hand in hand to bolster an organization’s defensive capabilities against cyber-attacks. Here are the differences between red and blue teams:
Red Team
The cybersecurity red team is composed of specialized personnel hired for their ethical hacking skills to find vulnerabilities in an organization’s security measures. Red team security consists of offensive security experts specialized in penetration testing of different systems. One of the critical phases in the development of a defensive mechanism against unauthorized intrusions is the testing stage. The testing phase involves the staging of comprehensive attacking exercises against the defensive mechanism to assess its effectiveness — people tasked with carrying out these exercises belong to a red team. They leverage their attacking skills to uncover any weakness in technology, people, and processes that may lead to unauthorized access to an organization’s digital estate.
Here are some common examples of red team security exercises:
- Penetration testing
Also referred to as ethical hacking, penetration testing is an activity where a red team tries to probe and infiltrate a secured system. - Social engineering
A process through which a red team tries to dupe an organization’s employee into providing access to a secured system. - Phishing
A red team acts by sending spoofed emails to an organization’s employees in an attempt to dupe them into clicking a fraudulent link that requests them to provide their login credentials.
Blue Team
Blue team security involves a team of professionals responsible for devising and executing preventive mechanisms against unauthorized intrusions. A blue team is responsible for defending against real threats and red teaming. In case of a successful intrusion from a real attacker or red team, members of the blue team are there to study the techniques used in the attack and develop preventive mechanisms that will prevent future attacks of the same type. The blue team is continuously engaged in strengthening the digital security infrastructure of an organization using programs such as Intrusion Detected Systems (IDS).
The following are the common exercises carried out under blue team cybersecurity:
- Carrying out DNS assessments to ensure that there are no phishing activities in the network or any general issue with DNS transactions.
- Conducting a footprint analysis to ensure that there are no unidentified signatures in the network that may signal a breach.
- Managing IDS, IPS, firewall access controls, and end-point security software on devices such as workstations.
>>[Request Demo] - Get the Hacker’s View Of Your Attack Surface
What are the benefits of having both Red and Blue teams?
Deploying the two groups allows an organization to leverage two different skill sets that have the same objective – thwarting unauthorized intrusions. It also creates a sense of competitiveness among the two different groups, thereby resulting in improved performance.
While the cybersecurity red team is valuable for identifying vulnerabilities in a computer network system, the expertise of the blue team is also required to fix those vulnerabilities. Therefore, both teams are indispensable.
For a successful cybersecurity setup, the two teams (red and blue) must keep a clear line of communication. The blue team must share the latest defensive security mechanisms with the red team; at the same time, the red team must share the latest threats, penetration practices, and latest red team hacking techniques.
Secondary teams in Information Security
While the red and blue team are the primary teams in cybersecurity, there are secondary teams that provide more support to the two teams; these are:
- Yellow team
The yellow team comprises the builders of software solutions. They are in charge of developing, testing, and deploying software. - Orange team
The orange team is involved in facilitation and training. They assist the yellow team w.r.t. cybersecurity. - Purple team
Purple team security consists of more of a dynamic party between red and blue teams than a unit. Its purpose is to maximize the capabilities of the primary teams. - Green team
The purpose of this team is to formulate policies and frameworks that guide how the primary teams interact. - White team
The white team comprises those in management and administration.
Conclusion
Efficient cybersecurity is an intricate web of dedicated teams working at multiple levels to secure an organization’s assets and IP from cyberattacks and malicious code. At FireCompass we provide Continuous Automated Red Teaming and Attack Surface Management to ensure your work continues uninterrupted.
FireCompass serves as a one-stop platform for automated and continuous recon, attack surface discovery, and launching multi-stage attacks to discover attack paths that are otherwise missed through conventional tools. Our nation-grade reconnaissance techniques constantly monitor new threats that crop up in the dark, deep, and surface web to stay ahead in the security game. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks mimicking the activities of a real attacker to identify breaches and attack paths.