Security teams are busy fixing CVEs, SQLi, and other critical vulnerabilities. However, exposing .git can potentially leak credentials, source code and other sensitive information. In this blog, we will uncover the dangers of hidden exposed .git, and how to identify and mitigate the relevant risk.
Introduction
In the realm of software development, Git stands as a pillar for version control, fostering collaboration, and enabling project management. However, exposing the .git directory can cause serious security issues. It’s like leaving the front door of your digital world wide open to potential threats. We will delve deep into the risks associated with exposed .git files and explore practical steps to secure the repositories.
Unmasking the .git Directory
The .git directory is a hidden core component situated at the root of a Git repository. It holds all the vital information required to manage the repository, commit history, configuration settings, branches, and references. Exposing this directory can have severe security consequences.
The Security Implications
Information Leakage:
When the .git directory is exposed, an attacker gains access to valuable information regarding the repository’s history and structure. This binds commit messages, usernames, email addresses, and potentially sensitive project-related data, offering malicious actors the tools to exploit vulnerabilities.
Code Theft:
An exposed .git directory permits attackers to download the entire repository, compromising access to the project’s source code. This jeopardizes the confidentiality and integrity of sensitive projects, potentially leading to intellectual property theft.
Security Vulnerabilities:
Exposing the .git directory elevates the risk of security vulnerabilities being uncovered and exploited. With access to the repository’s history, an attacker can identify outdated libraries, dependencies, or other weaknesses that might not be immediately apparent.
>> Discover & Test your Ransomware Attack Surface
How is .git Exposed?
Web Servers and Misconfigured Permissions:
One common way the .git directory is exposed is through web servers. Misconfigured permissions or web server configurations may inadvertently allow users to access the .git directory, even though it should be protected.
To check for .git exposure, use the following curl command:
curl -Is https://example.com/.git/HEAD
If the .git directory is exposed, you’ll receive an HTTP response that includes information about the Git repository.
Also a DotGit extension can be used. (DotGit)
Directory Listing:
If directory listing is enabled on a web server and the .git directory is not explicitly blocked, it can be accessed simply by navigating to the repository’s URL.Here, through Directory listing, we can also try to exploit Path Traversal vulnerability.
.gitignore Oversight:
The .gitignore file is used to specify which files and directories should be ignored by Git. However, if the .gitignore file itself is misconfigured or not in place, the .git directory may be inadvertently included in the repository.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Different Ways to Find Exposed .git Files
Manual Inspection:
The simplest method is to manually inspect websites and repositories for exposed .git directories. Navigate to the root of the repository’s URL and check if the .git directory is accessible. If it is, the repository is exposed.
Automated Scanning with GitTools:
GitTools, a powerful suite of Git-related tools, empowers Red Teamers to automate the discovery of exposed .git directories. The GitTools suite includes Dumper and Extractor, which can be used to search for and extract information from exposed .git repositories.
To search for exposed .git directories, use GitTool’s Dumper:git clone https://github.com/internetwache/GitTools
cd GitTools/Dumper
python gitdumper.py https://example.com/.git/ local-path-to-save-repo
Leveraging Google Dorking:
We can use Google Dorking techniques to discover exposed .git directories. Search for the following query in Google:
Inurl:.git
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Interesting Findings in an Exposed .git Directory
Commit History:
The commit history in an exposed .git directory provides Red Teamers with insights into the project’s development timeline, including the sequence of changes, the author of each change, and commit messages that may reveal sensitive information.
To explore the commit history, use the following command within the cloned repository:
git log
This command displays a detailed list of commits, authors, dates, and messages.
Configuration Files:
The .git directory also contains configuration files that may include valuable data such as repository URLs, credentials, and other settings. These can be viewed using the cat command:
cat .git/config
Review the configuration settings for any potential security weaknesses.
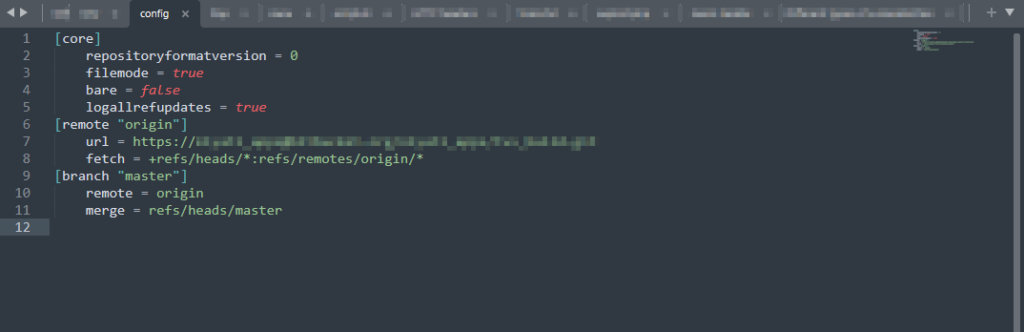
The config file may contain valuable information, such as the URL depicted in the above image. Successful Git cloning of this file could potentially grant access to the source code. In such cases, it may be necessary to employ techniques like brute forcing or hash cracking to obtain the password if authentication is required during the Git cloning process.
Branches and References:
The .git directory stores information about branches, tags, and references, allowing Red Teamers to understand the structure of the repository and potential entry points.
List branches with:
git branch -a
Explore the repository’s references and tags with:
git show-ref
Lateral Movement
Social Engineering:
The information gained from exposed .git directories can be utilized to craft highly personalized spear-phishing campaigns. Red Teamers can leverage insights into the development team’s activities, project specifics, and interpersonal dynamics to create convincing attack scenarios.
Code Analysis:
With access to the source code, Red Teamers can conduct an in-depth analysis of the project. This involves scrutinizing the codebase for vulnerabilities, misconfigurations, or hidden backdoors. These findings can serve as entry points for unauthorized access or privilege escalation within the target environment.
Foothold Establishment:
Infiltrating a target organization’s Git repository provides Red Teamers with a foothold in the development environment. This strategic advantage can be leveraged for further reconnaissance and lateral movement within the organization.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Conclusion:
Exposing the .git directory of a Git repository is a goldmine, unlocking a wealth of data for reconnaissance and potential exploitation. As Red Teamers, exploiting such exposures becomes a key strategy in identifying and exploiting security weaknesses within a target organization. Careful reconnaissance, analysis, and exploitation of these exposed .git files can pave the way for a successful breach.
By: FireCompass Delivery Team – K Surya Sai Harsh, Arnab Chattopadhayay , Amit Da, Joy Sen
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.