This week from October 30 to November 3, FireCompass research identified a significantly high number of CVEs that are High in severity and can be attributed to ransomware, botnets, and other threat actors groups which are creating significant impact. In this blog, we will share the important CVEs discovered this week as well as a list of malwares, threat actors and botnets which were most active this week along with the CVEs that they were using in their campaigns.
The Key Vulnerabilities that FireCompass has Focused on are:
- CVE-2023-46604 – Apache ActiveMQ
- CVE-2023-4967 – NetScaler ADC and NetScaler Gateway
- CVE-2023-46509 – Contec SolarView Compact
- CVE-2023-46490 – Cacti
- CVE-2023-46215 – Apache Airflow Celery provider
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2023-46604 – Apache ActiveMQ
Apache ActiveMQ is vulnerable to Remote Code Execution.The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath. Users are recommended to upgrade to version 5.15.16, 5.16.7, 5.17.6, or 5.18.3, which fixes this issue.
Here are the industries and companies that are affected by this CVE.
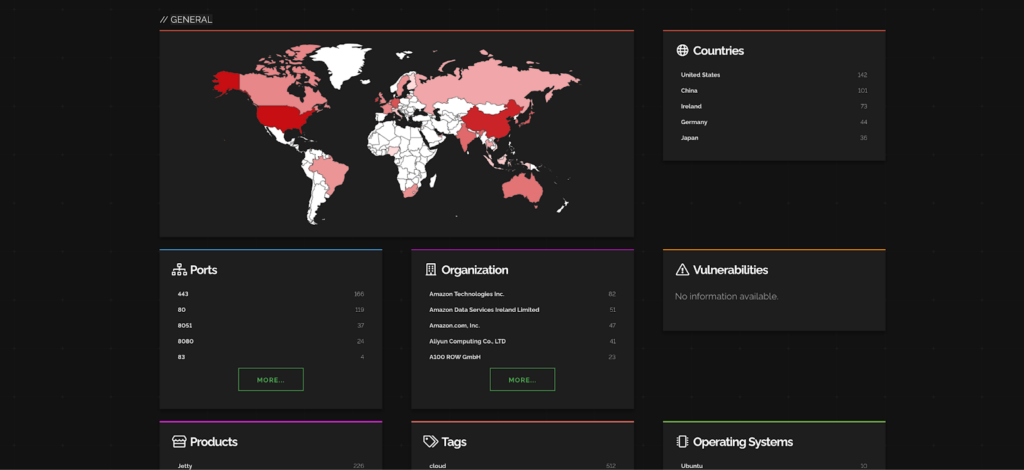
Ref: Shodan
Most impacted countries are USA and China while Amazon Services are getting affected the most.
>> Discover & Test your Ransomware Attack Surface
CVE-2023-4967 – NetScaler ADC and NetScaler Gateway
CVE-2023-4967 is a denial-of-service (DoS) vulnerability in Citrix NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA Virtual Server.
An attacker could exploit this vulnerability by sending a specially crafted request to an affected device. This could cause the device to crash or become unresponsive, making it unavailable to legitimate users.
Citrix has released security patches for CVE-2023-4967. Users should upgrade to the latest version of NetScaler ADC or NetScaler Gateway as soon as possible.
Here are the industries and companies that are affected by this CVE.
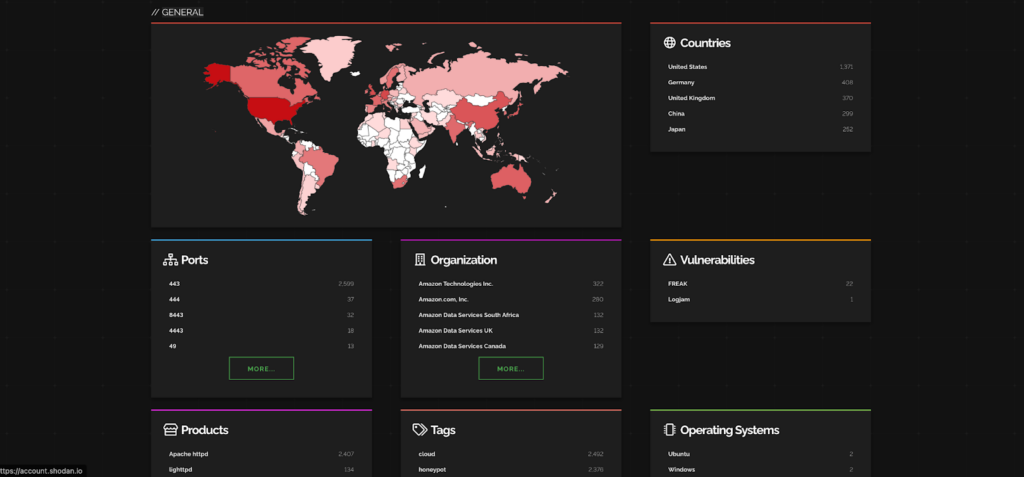
Ref: Shodan
Most impacted countries are USA and Germany while Amazon Services are getting affected the most.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
CVE-2023-46509 – Contec SolarView Compact
CVE-2023-46509 is an arbitrary code execution vulnerability in Contec SolarView Compact v.6.0 and before.
This vulnerability allows an attacker to execute arbitrary code on an affected device by sending a specially crafted request to the texteditor.php component. This could allow an attacker to take control of the device or steal sensitive data.
Contec has not released a patch for CVE-2023-46509 at this time. Users of Contec SolarView Compact should upgrade to a different product if possible.
Here are the industries and companies that are affected by this CVE.
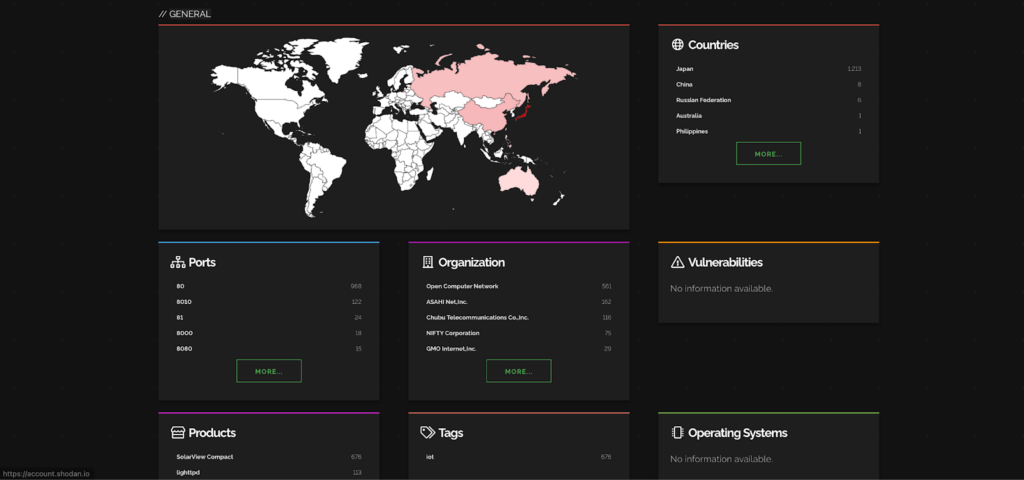
Ref: Shodan
Most impacted countries are Japan and China while Open Computer Network is getting affected the most.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
CVE-2023-46490 – Cacti
CVE-2023-46490 is a SQL injection vulnerability in Cacti v1.2.25 that allows a remote attacker to obtain sensitive information via the form_actions() function in the managers.php function.
An attacker could exploit this vulnerability by sending a specially crafted request to an affected device. This could allow the attacker to view or modify data in the Cacti database, including user accounts, passwords, and other sensitive information.
The Cacti team has released a patch for CVE-2023-46490. Users of Cacti v1.2.25 should upgrade to the latest version as soon as possible.
POC of the above code: https://gist.github.com/ISHGARD-2/a95632111138fcd7ccf7432ccb145b53
Here are the industries and companies that are affected by this CVE.
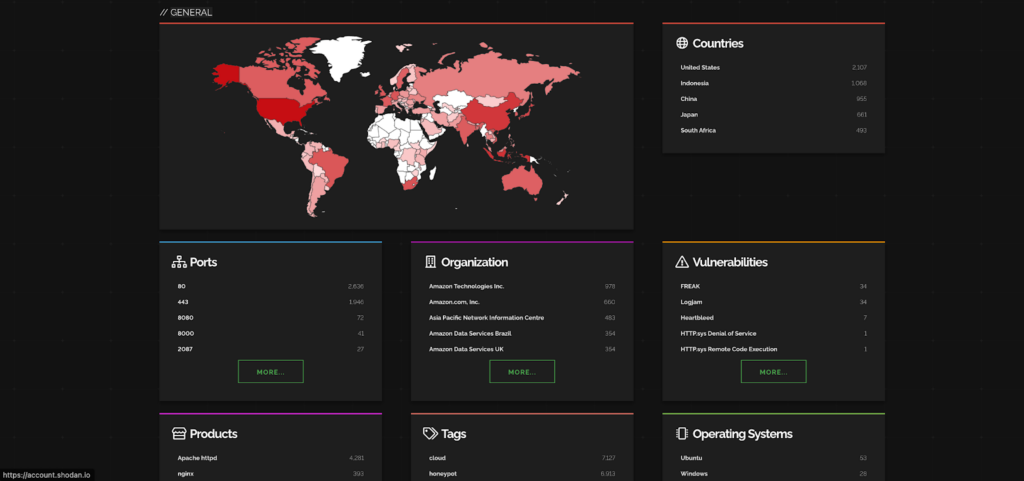
Ref: Shodan
Most impacted countries are USA and Indonesia while Amazon Services are getting affected the most.
CVE-2023-46215 – Apache Airflow Celery provider
CVE-2023-46215 is an information disclosure vulnerability in Apache Airflow Celery provider and Apache Airflow. It allows an attacker to obtain sensitive information, such as passwords, API keys, and other credentials, that is logged in clear text when using the rediss, amqp, or rpc protocols as the Celery result backend.
This vulnerability affects Apache Airflow Celery provider versions 3.3.0 through 3.4.0 and Apache Airflow versions 1.10.0 through 2.6.3.
To mitigate this vulnerability, users should upgrade to Apache Airflow Celery provider version 3.4.1 or later and Apache Airflow version 2.7.0 or later.
Here are the industries and companies that are affected by this CVE.
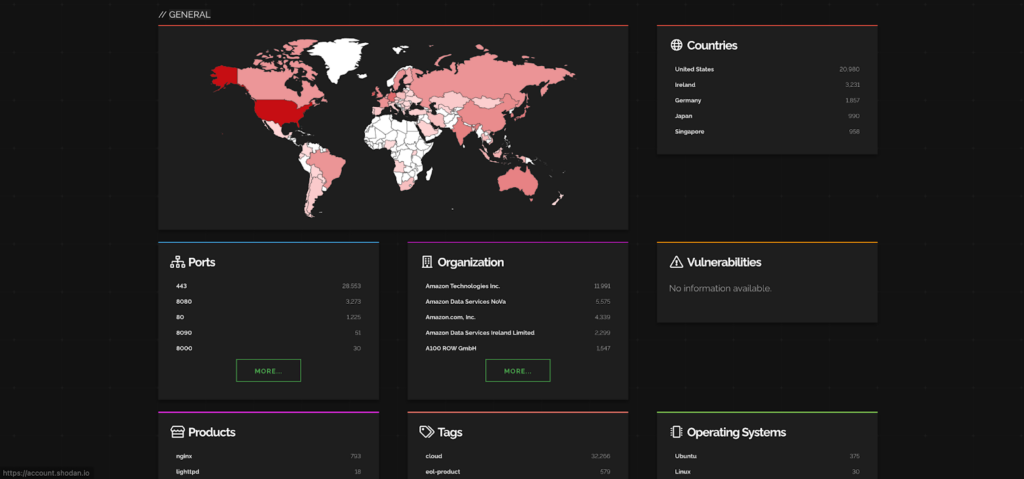
Ref: Shodan
Most impacted countries are USA and Ireland while Amazon Services are getting affected the most.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





