This week from October 23 to October 26, Firecompass research identified a significantly high number of CVEs that are High in severity and can be attributed to ransomware, botnets, and other threat actors groups which are creating significant impact. In this blog, we will share the important CVEs discovered this week as well as a list of malwares, threat actors and botnets which were most active this week along with the CVEs that they were using in their campaigns.
The Key Vulnerabilities that FireCompass has Focused on are:
- CVE-2023-20273 – Cisco IOS XE
- CVE-2023-34048 – VMware VCenter
- CVE-2023-37265, CVE-2023-37266 – CasaOS Multiple Vulnerability
- CVE-2023-46288 – Apache Airflow
- CVE-2023-45998 – Kodbox
The Key Malwares and Threat Actors that FireCompass has Focused on are:
- CVE-2021-40539 – AvosLocker Ransomware
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Know The Vulnerabilities Impacting Key Industries and Companies:
CVE-2023-20273 – Cisco IOS XE
CVE-2023-20273 is a command injection vulnerability in the Cisco IOS XE Web UI. It allows an authenticated attacker to inject arbitrary commands as the root user.
This vulnerability can be exploited by an attacker who has already gained access to the Cisco IOS XE device, for example by exploiting another vulnerability such as CVE-2023-20198. Once the attacker has gained access, they can use CVE-2023-20273 to escalate their privileges to root and take full control of the device.
Here are the industries and companies that are affected by this CVE.
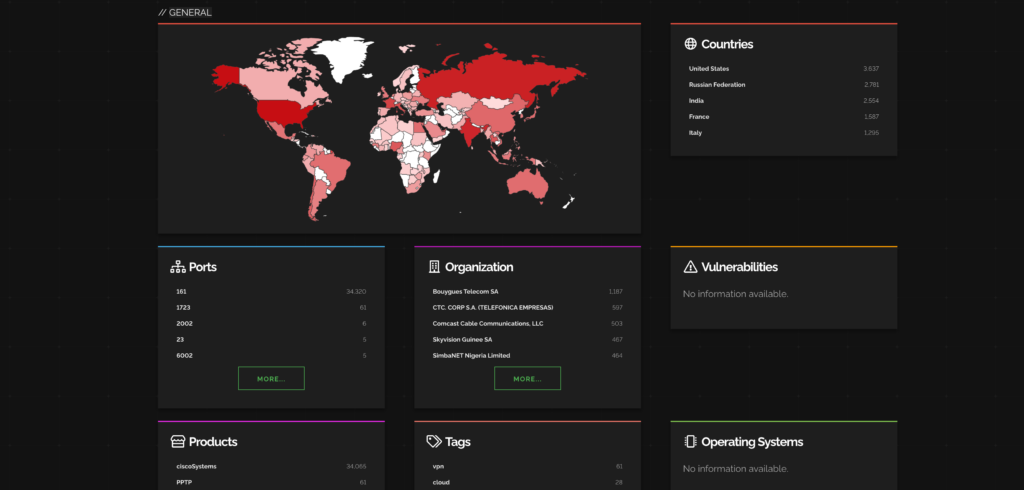
Ref: Shodan
Most impacted countries are USA and Russian Federation while telecom service providing companies are getting affected the most.
>> Discover & Test your Ransomware Attack Surface
CVE-2023-34048 – VMware VCenter
CVE-2023-34048 is a critical severity remote code execution (RCE) vulnerability in VMware vCenter Server. It allows an attacker with network access to the vCenter Server to trigger an out-of-bounds write, which could lead to arbitrary code execution on the target system.
This vulnerability is particularly dangerous because it does not require any authentication to exploit. An attacker could simply send a specially crafted packet to the vCenter Server over the network to trigger the vulnerability.
Here are the industries and companies that are affected by this CVE.
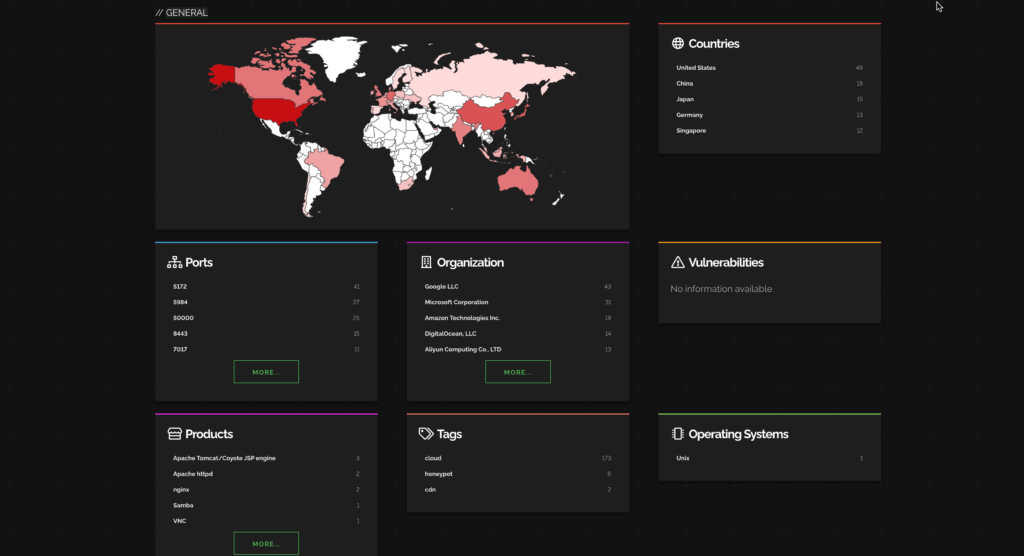
Ref: Shodan
Most impacted countries are US and China while the big tech giants (ie. Google, Microsoft, Amazon) are getting affected the most.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
CVE-2023-37265, CVE-2023-37266 – CasaOS Multiple Vulnerability
CVE-2023-37265 and CVE-2023-37266 are two critical severity vulnerabilities in CasaOS, an open-source personal cloud system. CasaOS Community-based open source software focused on delivering simple personal cloud experience around the Docker ecosystem. CasaOS is installed in raspberry pi. These vulnerabilities allow unauthenticated attackers to gain root access to CasaOS instances.
CVE-2023-37265 is an authentication bypass vulnerability that allows attackers to execute arbitrary commands as root without needing to authenticate. CVE-2023-37266 is a JSON Web Token (JWT) validation vulnerability that allows attackers to craft arbitrary JWTs and access features that usually require authentication.
These vulnerabilities are particularly dangerous because they allow attackers to gain complete control over CasaOS instances without any prior knowledge or access. Once an attacker has gained root access, they can steal data, install malware, or disrupt operations.
Here are the industries and companies that are affected by this CVE.
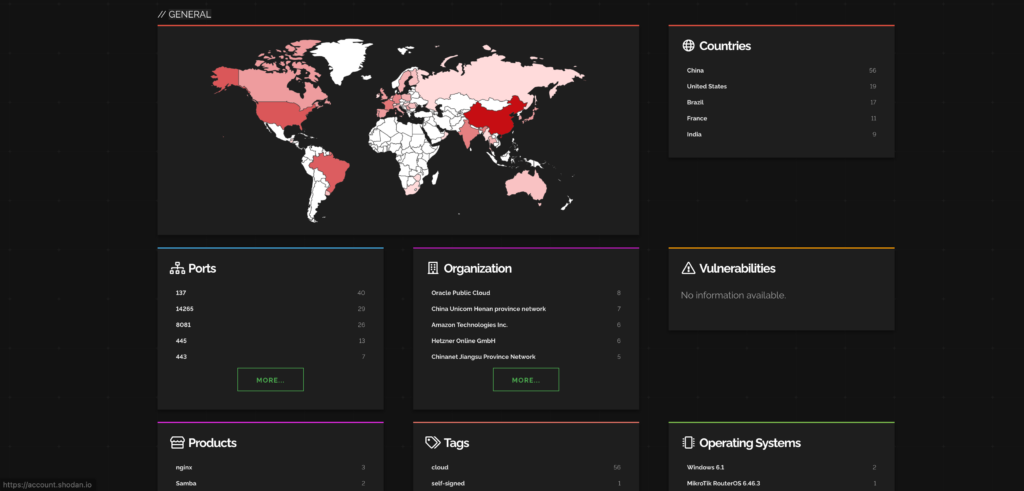
Ref: Shodan
Most impacted countries are China and USA while cloud service providers are getting affected the most.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
CVE-2023-46288 – Apache Airflow
CVE-2023-46288 is an information exposure vulnerability in Apache Airflow. It allows authenticated users with the ability to read configuration via the Airflow REST API to access sensitive configuration information, even when the expose_config option is set to non-sensitive-only.
This vulnerability is caused by a flaw in the way that Apache Airflow handles configuration requests. The vulnerable code does not properly filter the configuration information that is returned to the user, which can allow authenticated users to access sensitive information such as database passwords, API keys, and other secrets.
Here are the industries and companies that are affected by this CVE.
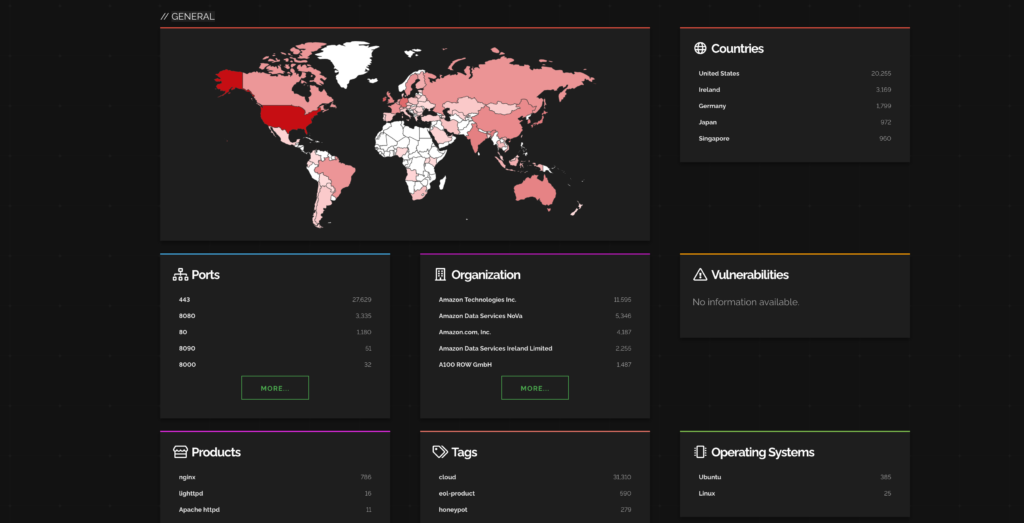
Ref: Shodan
Most impacted countries are the US and Ireland while Amazon is getting affected the most.
CVE-2023-45998 – Kodbox
CVE-2023-45998 is a Cross-Site Scripting (XSS) vulnerability in Kodbox 1.44. It allows an attacker to inject malicious code into the Kodbox web application, which can then be executed by other users.
This vulnerability can be exploited by an attacker by crafting a specially crafted request to the Kodbox web application. The request can contain malicious JavaScript code, which will be executed by the victim’s browser when they visit the Kodbox website.
The attacker can use this vulnerability to steal user cookies, redirect users to malicious websites, or even take control of the victim’s computer.
Here are the industries and companies that are affected by this CVE.
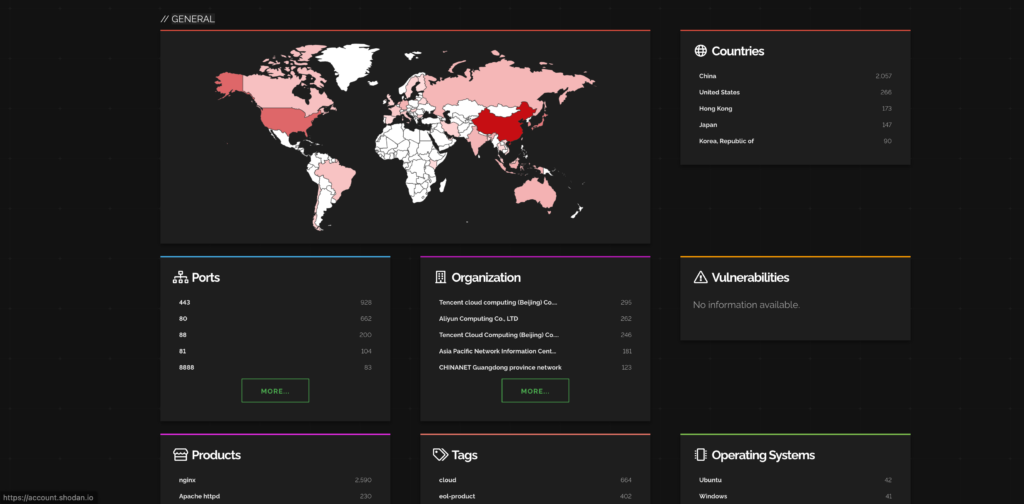
Ref: Shodan
Most impacted countries are China and USA while cloud service providers are getting affected the most.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2021-40539 – AvosLocker Ransomware
CVE-2021-40539 is a critical severity vulnerability in Zoho ManageEngine ADSelfService Plus version 6113 and prior. It is an authentication bypass vulnerability with resultant remote code execution. This means that an attacker can exploit this vulnerability to gain unauthorized access to a victim’s system and execute arbitrary code.
AvosLocker ransomware is a relatively new ransomware strain that has been targeting organizations of all sizes since mid-2021. It is known for using a variety of techniques to gain access to victim systems, including exploiting known vulnerabilities like CVE-2021-40539.
POC of the above code: https://packetstormsecurity.com/files/165085/ManageEngine-ADSelfService-Plus-Authentication-Bypass-Code-Execution.html
Here are the industries and companies that are affected by this CVE.
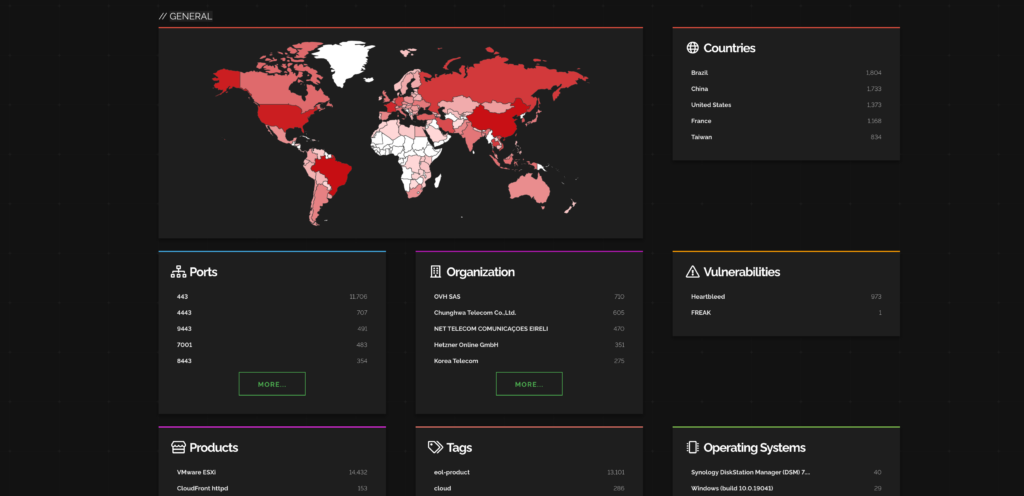
Ref: Shodan
Most impacted countries are Brazil and China while telecom service providers are getting affected the most.
References
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
- https://www.vmware.com/security/advisories/VMSA-2023-0023.html
- https://github.com/IceWhaleTech/CasaOS-Gateway/commit/391dd7f0f239020c46bf057cfa25f82031fc15f7
- https://github.com/IceWhaleTech/CasaOS/commit/705bf1facbffd2ca40b159b0303132b6fdf657ad
- https://lists.apache.org/thread/yw4vzm0c5lqkwm0bxv6qy03yfd1od4nw
- https://gist.github.com/fangjiuye/703fdb643db558640f23e4e7c9532348
- https://packetstormsecurity.com/files/165085/ManageEngine-ADSelfService-Plus-Authentication-Bypass-Code-Execution.html
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
References
- FireCompass Threat Intel Team
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- NVD CVE Feed
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





