
As per Threat Intel data published by IBM Xforce, 80% of the times, Ransomeware gets initial access using top 3 Attack Vectors – exploiting vulnerabilities contribute 26%, Shadow IT & Stolen Credentials contribute 16%, various variants of phishing attacks contribute 41%, and the rest by other attack vectors.
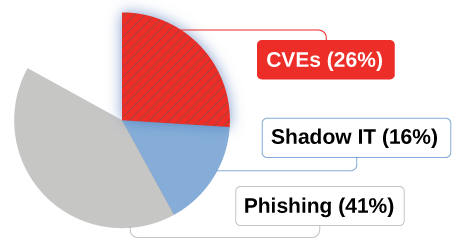
It means that Shadow IT Discovery, identifying and removing Shadow IT & Stolen Credentials, and identification and fixing attacker prioritized CVEs can reduce chances of ransomware attack by at least 42%.
In this article we will dive deep into the top 6 most critical and ransomware weaponized CVEs published in the last 3 Months. Identifying and fixing these CVEs, can straightway decrease the chance of Ransomware by 26%, assuming previous critical CVEs are already fixed.
Following CVEs are published by global security research community. Ransomware groups and APT target many of these vulnerabilities to get Initial Access. All the vulnerabilities have Proof of Concepts (PoC) exploit code publicly available on GitHub. That means it is easy for attackers to target the organizations with the exposed assets these vulnerabilities target.
Key Ransomware Tracked by FireCompass:
| Ransomware | Exploit |
|---|---|
| Clop Ransomware | Uses Fortra Anywhere MFT Command Injection vulnerability to install itself on target machine |
| Magniber Ransomware | Uses recent critical Microsoft Windows vulnerabilities to install itself onto the target machine. |
| Lockbit Ransomware | Use recent ZK framework RCE to get installed on target machines. |
| New ESXiArgs Ransomware | Uses an old Unauthenticated heap overflow in OpenSLP service in ESXi servers to deliver itself onto the target machines |
| Hive Ransomware | Although this ransomware is not using any new CVEs, but it is exploiting some old vulnerabilities in the Microsoft Exchange services to get itself installed on the target machine |
| Dark Power Ransomware | Although this ransomware is delivering itself using only phishing, it impacted more than 10 organizations due to its architecture and inability of the firewalls and security personnels to detect it. |
To remain safe against these critical vulnerabilities, it is imperative that organizations find and fix them at the earliest. The Firecompass Research Team urges organizations to identify their exposed assets, test for vulnerabilities, and fix any issues that are discovered. The Firecompass platform for Continuous Automated Red Teaming & External Attack Surface Management can find and test all those vulnerabilities, as well as other critical vulnerabilities on our customers’ network, as soon as they are discovered.
Technical Details:
Clop Ransomware:
Clop aka Cl0p is one of the most notorious Ransomware As A Service(RaaS) which is operated by Russian speaking groups. Many affiliates like TA505 have been spotted deploying Clop ransomware to attack organizations around the world. They resort to using double-extortion techniques and auctioning off the stolen information on the dark web. In February 2023, Clop ransomware was used to target and extort organizations using a zero day mentioned below.
CVE-2023-0669 – Forta GoAnywhere Command Injection
In February 2023, GoAnyWhere MFT file transfer solutions developers warned customers that a zero-day RCE is being exploited in the wild by the Clop Ransomware.
Forta GoAnywhere MFT suffers from a pre-authentication command injection vulnerability in the License Response Servlet due to deserializing an arbitrary attacker-controlled object.
This CVE has been exploited by the Clop ransomware in the wild as an initial stage to gain remote code execution and load the ransomware on the target machines.
Magniber Ransomware:
Magniber which is Ransomware As A Service (RaaS) which has been resurfaced in 2021 after being first detected nearly six years ago. From then on, malicious attackers have been using Magniber to attack organizations.
In October 2022, it is observed that the Magniber ransomware has been deployed in a phishing campaign using recent CVE which is mentioned below.
CVE-2022-44698 – Windows SmartScreen Security Feature Bypass
In 2022, Microsoft released an advisory about a vulnerability found in the Window’s SmartScreen feature which allows an attacker to bypass it’s security features.
This CVE was used by Magniber to malformed a digital signature block to bypass execution blocks by Mark Of The Web(MOTW) which is designed to protect users from untrusted sources, allowing malicious files to be loaded into the target system without raising alerts. CVE-2023-24880 which is a variant of CVE-2022-44698 is also being used by ransomware actors to load the ransomware onto the target machines.
LockBit 3.0 Ransomware:
Lockbit 3.0 aka Bitwise Spider is one of the most notorious and active Ransomware As A Service(RaaS) in the cybercriminal arena. This Russian speaking ransomware gang began their operations in September 2019 and their affiliates are known to target large numbers of victims and currently have the highest reputation in the cybercriminal underground network. Lockbit 3.0 has gone through a lot of transition and rebranding which can be visualized below.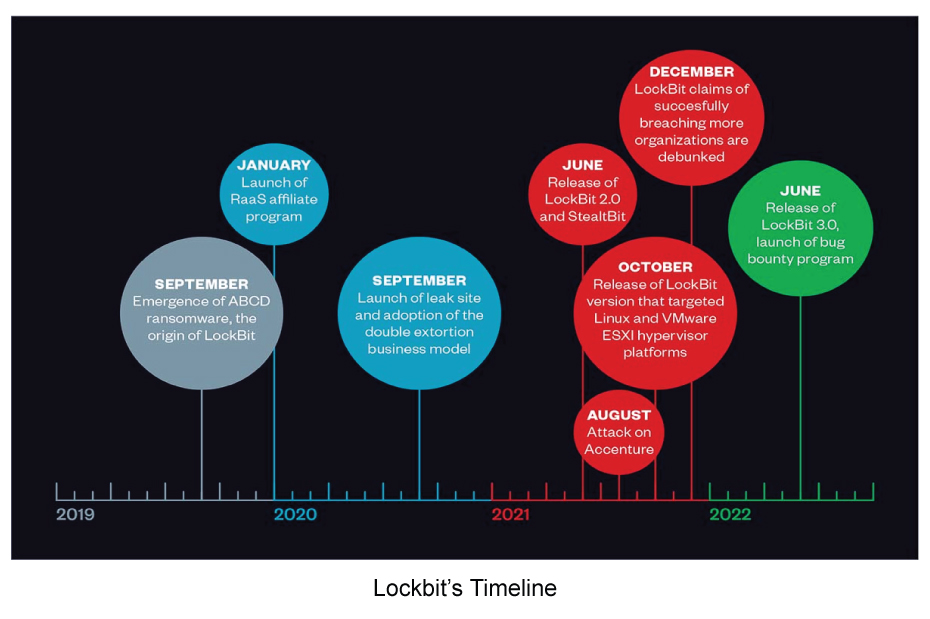
For initial access, Lockbit and its affiliates used varieties of vectors like leaked RDP credentials, known exploits and social engineering. In March 2023, we observed that Lockbit had used a vulnerability that is quite interesting.
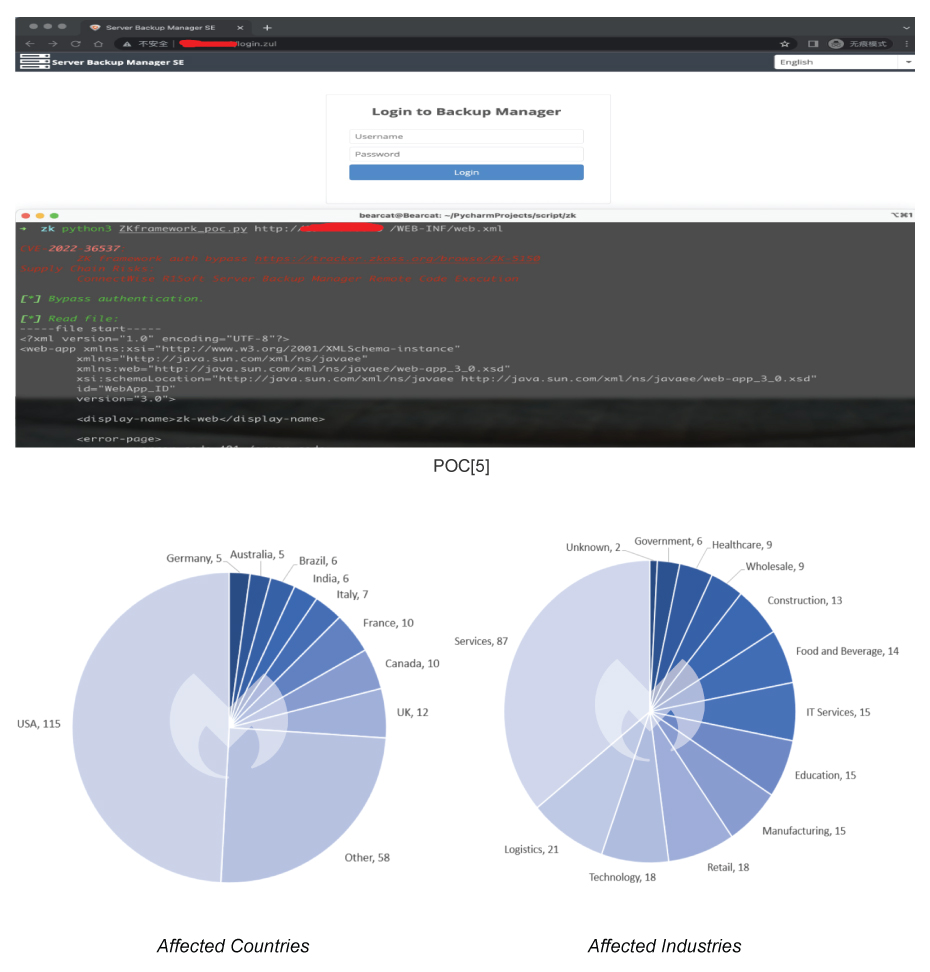
CVE-2022-36537 – ZK Framework Information Disclosure.
It is observed that the ZK Framework which is a Java Framework v9.6.1, 9.6.0.1, 9.5.1.3, 9.0.1.2 and 8.6.4.1 allows attackers to access sensitive data. This issue arises in the framework’s AuUploader component that allows the attacker to forward an HTTP request to an internal URI. However, in the context of the popular ConnectWise R1Soft server, it leads to an RCE.
Recently, the LockBit 3.0 ransomware used this vulnerability to gain initial access to deploy their ransomware payloads. The steps performed for this are:
- The exploitation of the vulnerability to first bypass the authentication.
- Deployment of the malicious JDBC driver to obtain RCE and backdoor access.
- REST API to issue commands to malicious C2 servers to deploy ransomware payloads.
New ESXiArgs Ransomware:
New ESXiArgs ransomware strain (not the same as the old ESXiArgs ransomware) appears to be from a new ransomware family, not from the Nevada Ransomware. Unlike the previous version of ESXiArgs ransomware, the ransom notes seen in this attack do not appear to be related to the Nevada Ransomware. The newer version has infected more than 2,100 VMware servers to date. As the name suggests, this ransomware encrypts files with extensions, related to vmware and creates a .args file for each encrypted document with metadata (likely needed to be decrypted).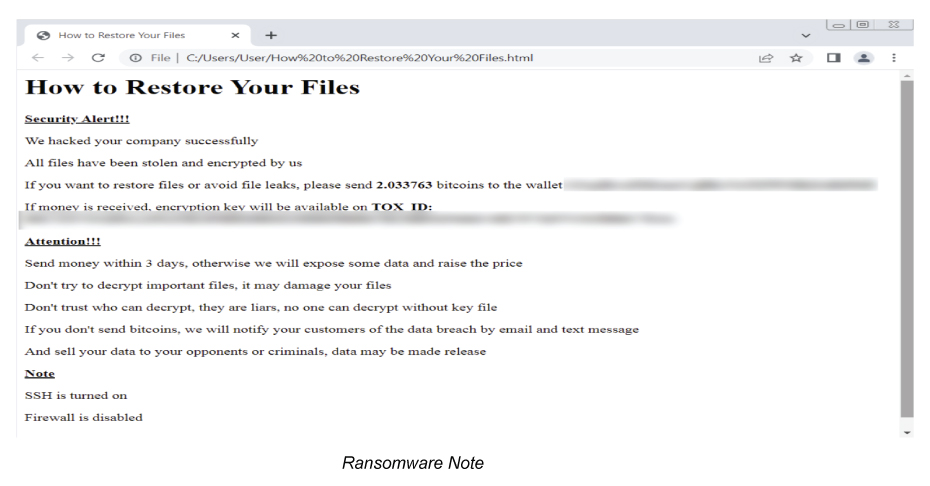
CVE-2021-21974 – VMware’s OpenSLP service heap-overflow vulnerability.
According to Security Researchers, the threat actors are supposed to be exploiting an old and known heap-overflow vulnerability in VMware’s OpenSLP service in order to gain initial access to the victim machine.
Hive Ransomware:
Hive ransomware has become one of the most active ransomware families since its discovery in June 2021. It gains access to a network through phishing emails with malicious attachments and then spreads laterally through the network and side by side continues to steal unencrypted files. It treated Microsoft Exchange as an entry point. After gaining admin access on a domain controller, the ransomware is executed to encrypt all devices. The HIVE group then deletes backups in order to prevent victims from recovering their data (double extortion technique).- CVE-2021-34473 – Remote code execution in Microsoft Exchange server: Microsoft Exchange Server is vulnerable to remote code execution. CVE-2021-34523, a variant of CVE-2021-34473 is also being abused by Hive.
- CVE-2021-31207 – Microsoft Exchange Server Security Bypass: Microsoft Exchange Server is also vulnerable to a Security Bypass technique which was abused by Hive.
- CVE-2021-33558 – Sensitive information disclosure via misconfiguration in Boa File Server: Hive ransomware exploited the Boa server vulnerability to get Sensitive information by taking advantage of the misconfiguration involving backup.html, preview.html, js/log.js, log.html, email.html, online-users.html, and config.js. They mostly exploited this vulnerability to target energy grids in India.
Dark Power Ransomware
This newest player in the block has burst onto the scene with vigor, breaching at least 10 organizations in less than a month’s time.The group which uses a double extortion technique, has added to its body count in Algeria, the Czech Republic, Egypt, France, Israel, Peru, Turkey, and the US, across the agricultural, education, healthcare, IT, and manufacturing sectors.
The group, which Trellix researchers have named “Dark Power,” is in most ways like any other ransomware group. But it separates itself from the pack due to sheer speed and lack of tact – and its use of the Nim programming language.
It sets a classic example of where ransomware gangs are using new programming languages rather than recorded vulnerabilities to hide their presence and get installed onto the target machine. Dark Power utilizes Nim, an efficient, expressive and elegant language which has become more prevalent with regards to malware creation. Nim being a very new language most of the firewalls and security tools lack the signatures to detect malicious nim binaries.It is considered as a niche choice by the malware developers that is unlikely to be detected by the defense tools.
Upon execution, the ransomware creates a randomized 64 character long ASCII string for initializing the encryption algorithm with a unique key on each execution. This is followed by stopping all the backup services and anti-malware products present in its hardcoded list. After all of the above services are killed, the ransomware sleeps for 30 seconds and clears the console and Windows system logs to prevent analysis from data recovery experts.
The encryption uses AES (CRT mode) and the ASCII string generated upon launch. The resulting files are renamed with the “.dark_power” extension. System-critical files like DLLs, LIBs, INIs, CDMs, LNKs, BINs, and MSIs, as well as the Program Files and web browser folders, are excluded from encryption to keep the infected computer operational, thus allowing the victim to view the ransom note and contact the attackers.
Another interesting fact about this ransomware is that the ransom note is not a single page note but rather a 8 page long pdf outlining the execution of the attack followed by ransom demands and contact details.
The unique thing about Dark Power that makes it more dangerous from the other ransomware is that it first deletes the backup servers on the target environment and then began it’s actual encryption of the files, which causes double damage to the target organizations.
These are some of the major Ransomwares which have been exploited in the wild in recent times and are still being exploited constantly as has been reported by some of the research organizations.
Our research team constantly keeps an eye on the latest upcoming CVEs and exploits and keeps track of them on a regular basis, notifying our customers and helping them mitigate the risks.
By: Firecompass Research Team
References
- Firecompass Threat Intel Team
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- NVD CVE Feed
- https://github.com/0xf4n9x/CVE-2023-0669
- https://github.com/Malwareman007/CVE-2022-36537
- https://www.bleepingcomputer.com/news/security/new-dark-power-ransomware-claims-10-victims-in-its-first-month/
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





