This week from November 20 to November 24, Firecompass research identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and somenew & well known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns. Also this week there was Microsoft Patch Tuesday of the month as well
The Key Vulnerabilities That FireCompass Has Focused On Are:
- CVE-2023-48029 – CoreBos CSV Injection
- Adobe Coldfusion Vulnerabilities
- CVE-2023-43177 – CrushFTP Remote Code Execution
- CVE-2023-22516 – Bamboo Data Center and Server RCE
- CVE-2023-22521 – Crowd Data Center and Server RCE
- OwnCloud Vulnerabilities
- CVE-2021-22150 – Kibana server RCE
The Key Malwares And Threat Actors That FireCompass Has Focused On Are:
- CVE-2023-46604 – Apache ActiveMQ
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Know The Vulnerabilities Impacting Key Industries and Companies:
CVE-2023-48029 – CoreBos CSV Injection
CoreBos is an open-source and free business application framework that helps small and medium businesses to handle all the day to day tasks. Corebos 8.0 and below is vulnerable to CSV Injection. An attacker with low privileges can inject a malicious command into a table. This vulnerability is exploited when an administrator visits the user management section, exports the data to a CSV file, and then opens it, leading to the execution of the malicious payload on the administrator’s computer.
POC Link – https://nitipoom-jar.github.io/CVE-2023-48029/
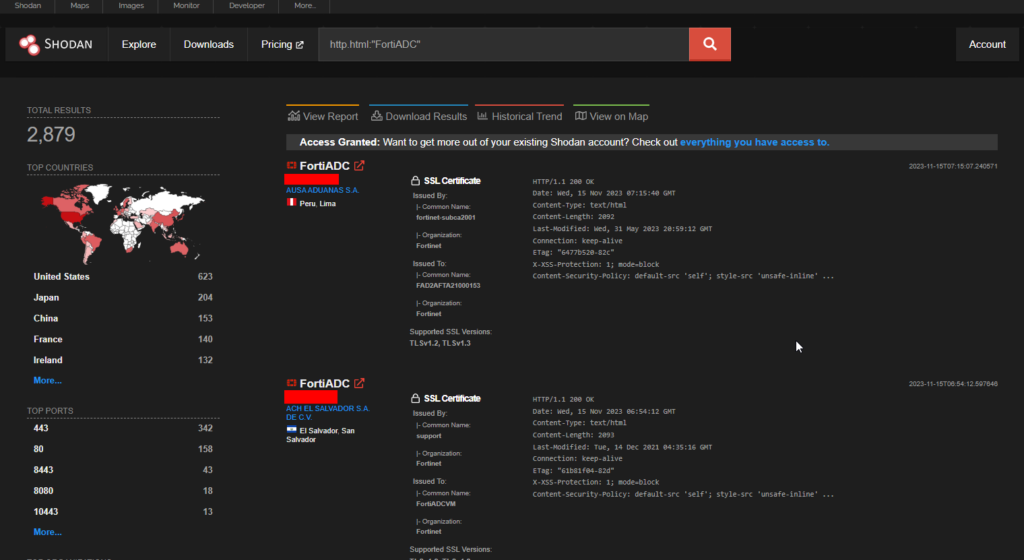
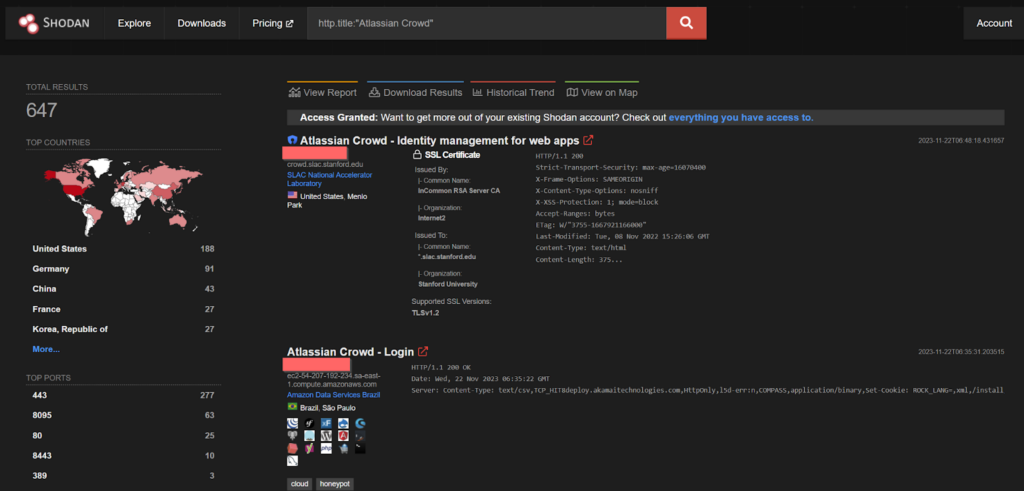
Shodan shows 2879 endpoints and the USA has the most number of them.
Adobe Coldfusion Vulnerabilities
Adobe Coldfusion is a popular web application development tool which had a fair share of vulnerabilities this year along with various threat actors abusing it. This week it released five CVEs in version 2023.5
- CVE-2023-26347 – Improper Access Control vulnerability
- CVE-2023-44350 – Deserialization to RCE
- CVE-2023-44351 – Deserialization to RCE
- CVE-2023-44352 – Reflected Cross-Site Scripting (XSS)
- CVE-2023-44353 – Deserialization to RCE
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2023-43177 – CrushFTP Remote Code Execution
CrushFTP Server is a multipurpose FTP server. The version prior to 10.5.1 is vulnerable to Improperly Controlled Modification of Dynamically-Determined Object Attributes leading to remote code execution.
POC – https://convergetp.com/2023/11/16/crushftp-zero-day-cve-2023-43177-discovered/
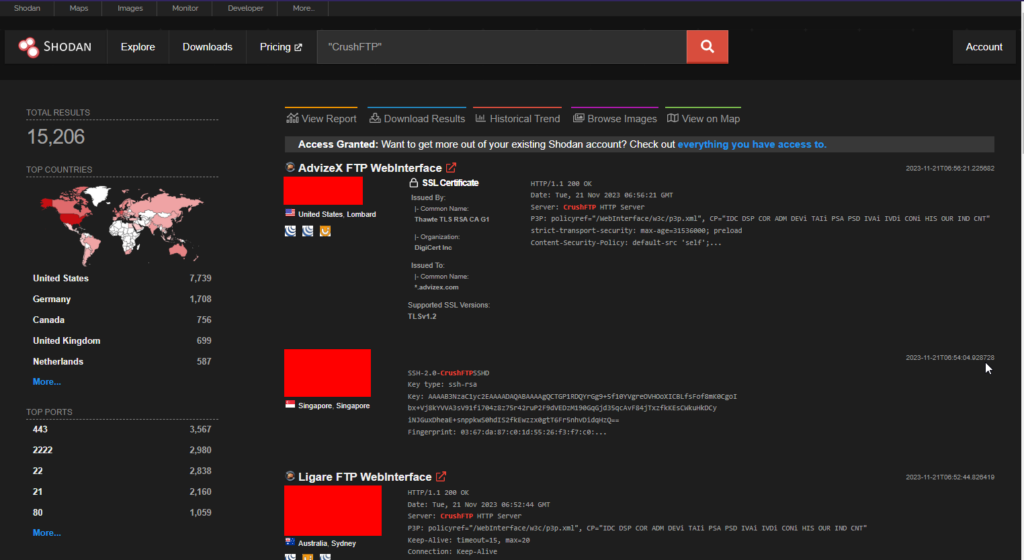
At least 15000 CrushFTP endpoints are exposed on Shodan.
CVE-2023-22516 – Bamboo Data Center and Server Remote Code Execution
This High severity RCE (Remote Code Execution) vulnerability was in Bamboo Data Center and Server. This RCE (Remote Code Execution) vulnerability allows an authenticated attacker to execute arbitrary code which has high impact to confidentiality, high impact to integrity, high impact to availability, and requires no user interaction.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2023-22521 – Crowd Data Center and Server Remote Code Execution
This High severity RCE (Remote Code Execution) vulnerability was introduced in version 3.4.6 of Crowd Data Center and Server. This RCE (Remote Code Execution) vulnerability allows an authenticated attacker to execute arbitrary code which has high impact to confidentiality, high impact to integrity, high impact to availability, and requires no user interaction.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
OwnCloud Vulnerabilities
CVE-2023-49104: ownCloud oauth2 Subdomain redirect
This vulnerability affects ownCloud owncloud/oauth2 before 0.6.1, when Allow Subdomains is enabled. An attacker can exploit this vulnerability to redirect callbacks to a Top Level Domain controlled by the attacker. This could allow the attacker to steal the victim’s session cookies, or to execute arbitrary code on the victim’s machine.The vulnerability is caused by the fact that ownCloud does not properly validate the redirect-url parameter. This allows an attacker to pass in a crafted redirect-url that points to a domain that they control. When the victim clicks on a link that contains the malicious redirect-url, they will be redirected to the attacker’s domain.
CVE-2023-49105: ownCloud Unauthenticated File Access
This vulnerability affects ownCloud owncloud/core before 10.13.1. It allows an attacker to access, modify, or delete any file without authentication if they know the username of the victim and the victim has no signing-key configured. This is because the system accepts pre-signed URLs even when the file owner has not configured a signing key. The earliest affected version is 10.6.0.
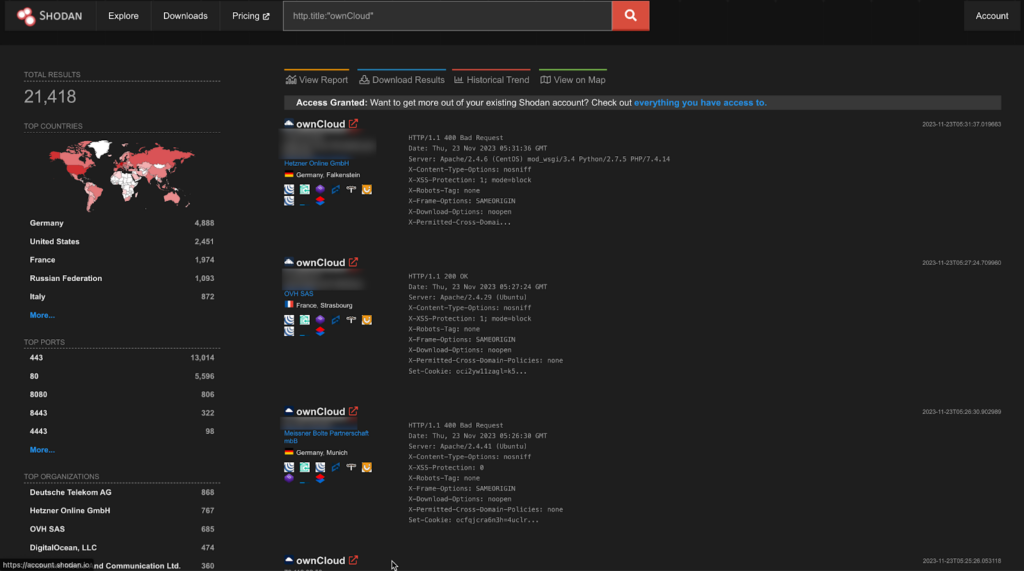
A staggering 21k endpoints are exposed on Shodan.
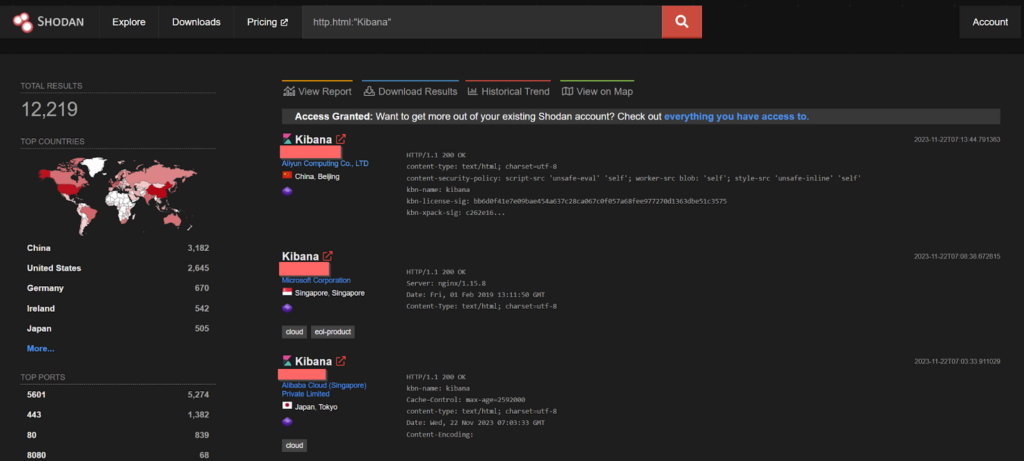
CVE-2021-22150 – Kibana server Remote Code Execution
This vulnerability was discovered when a user with Fleet admin permissions could upload a malicious package. Due to using an older version of the js-yaml library, this package would be loaded in an insecure manner, allowing an attacker to execute commands on the Kibana server.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
Important Weekly Threat Actors
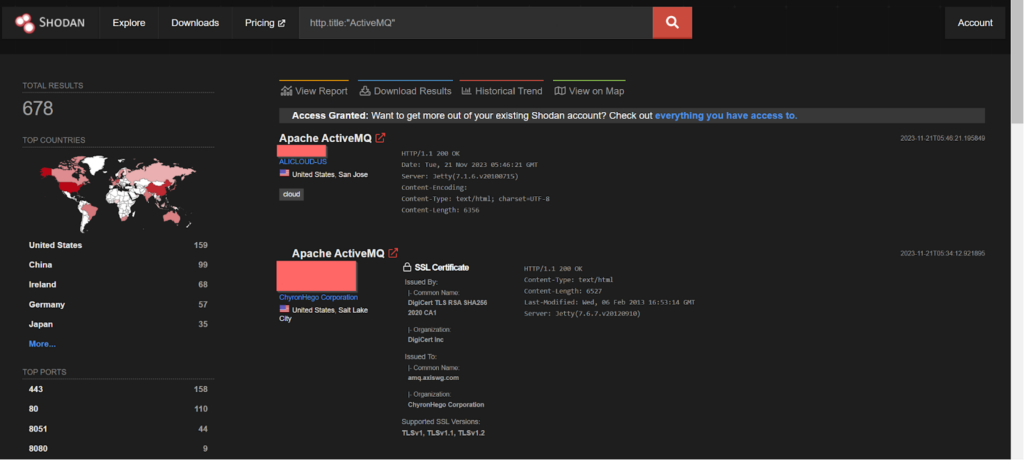
CVE-2023-46604 – Kinsing malware operator
The Java OpenWire protocol marshaller is vulnerable to Remote Code Execution. This vulnerability may allow a remote attacker with network access to either a Java-based OpenWire broker or client to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause either the client or the broker (respectively) to instantiate any class on the classpath. This vulnerability was found to be exploited by Kinsing malware operator, a malware family distributed by the H2Miner botnet, is known for targeting Linux-based infrastructure systems including Docker container hosts, Redis instances, and (in recent weeks) Salt servers.
The POC of the above vulnerability can be found here below:
https://github.com/X1r0z/ActiveMQ-RCE
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





