During the week spanning December 04 to 09, the FireCompass research team uncovered a substantial number of Common Vulnerabilities and Exposures (CVEs) marked as high severity. Notably, ransomware, botnets, and various threat actors were causing significant disruptions. Among the identified CVEs were vulnerabilities found in widely-used commercial products across various industries. Additionally, new and familiar malware strains were observed targeting different sectors throughout the week. In this overview, we will highlight the crucial CVEs that were discovered, along with a list of the most active malware, threat actors, and botnets, specifying the CVEs exploited in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2023-38003 – IBM DB2 unauthorized access
- CVE-2023-40460 – ALEOS client-side script execution
- CVE-2023-40461 – ALEOS cross-site scripting
- CVE-2023-48123 – Netgate Plus RCE
List Of Malwares And Threat Actors:
- CVE-2023-27350 – PaperCut NG/MF Unauthenticated Remote Code Execution’
- CVE-2023-42793 – JetBrain TeamCity Unauthenticated Remote Code Execution
- CVE-2023-50164 – Struts Remote Code Execution
Detailed Analysis: Vulnerabilities
CVE-2023-38003 – IBM DB2 Unauthorized Access
An unauthorized access vulnerability was found in the IBM DB2 which is a relational database developed by IBM. In the versions 10.5, 11.1 and 11.5 allows a user with “DATAACESS” privileges to execute routines which the user is not authorized to.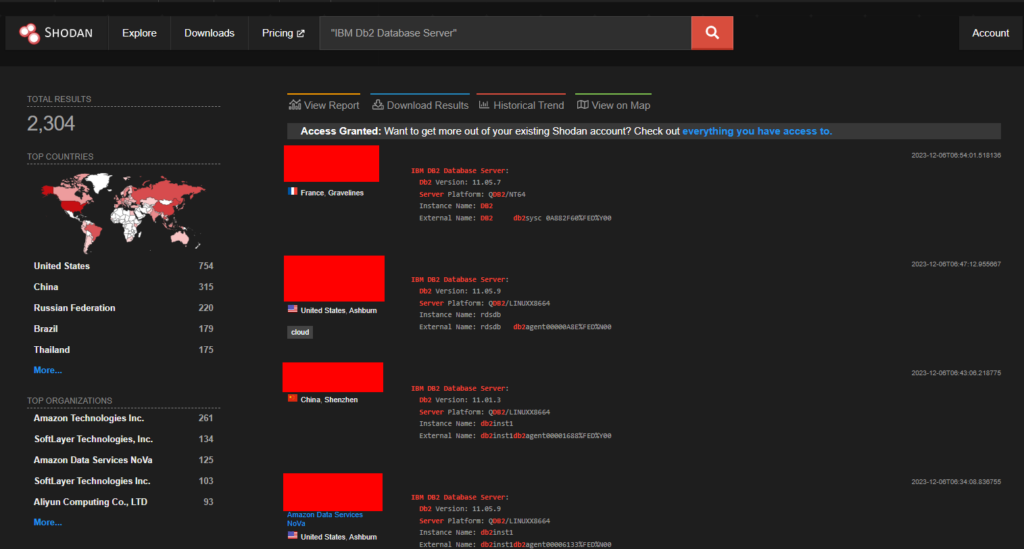
A total of 2,304 endpoints of IBM DB2 are exposed on the Shodan.
CVE-2023-40460 and CVE-2023-40461 – ALEOS Multiple Vulnerability
The ACEManager component of ALEOS does not validate uploaded file names and types, which could potentially allow an authenticated user to perform client-side script execution within ACEManager, altering the device functionality until the device is restarted.
The ACEManager component of ALEOS, allows an authenticated user with Administrator privileges to access a file upload field which does not fully validate the file name, creating a Stored Cross-Site Scripting condition.
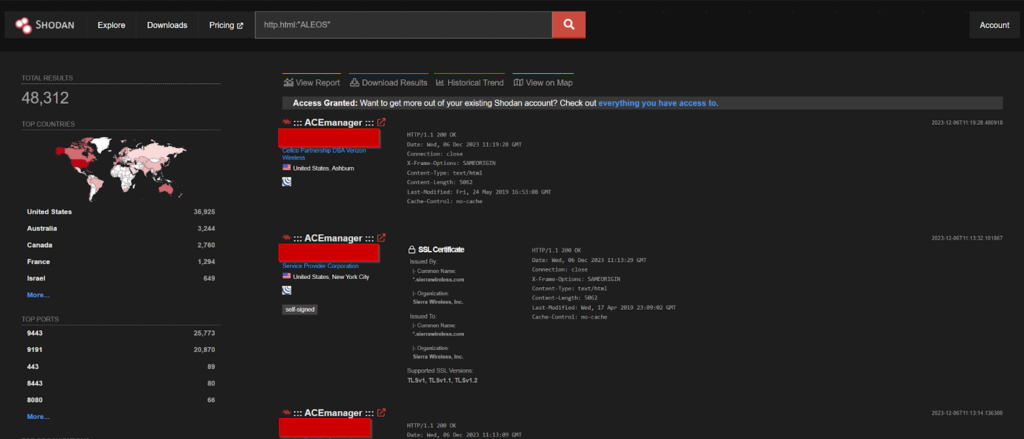
A total of more than 48k endpoints of ALEOS are exposed on the Shodan.
CVE-2023-48123 – NetGate Pfsense Plus
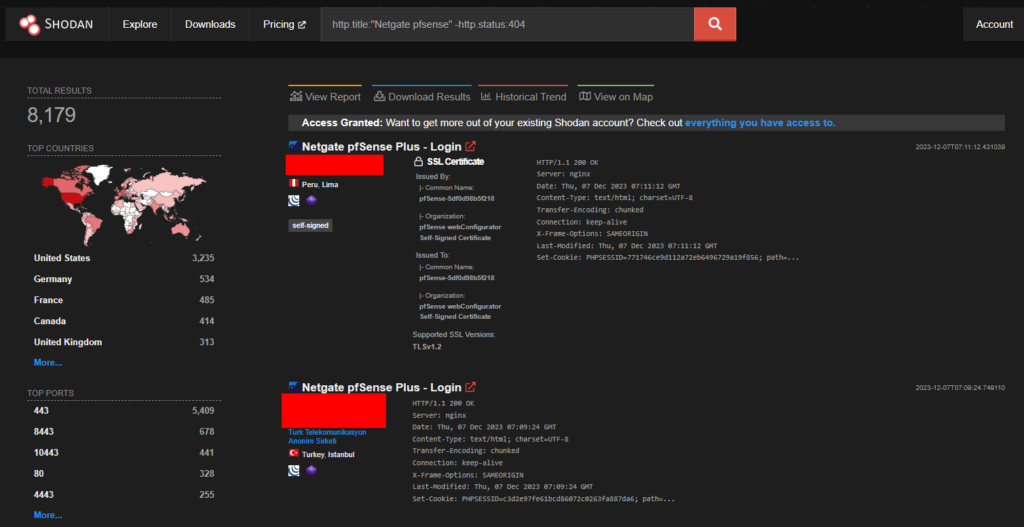
Approximately 8 thousand endpoints for Netgate Pfsense Plus are exposed on shodan.
Detailed Analysis: Threat Actors
CVE-2023-27350 – BlueSky Ransomware, Tor2Mine
This vulnerability allows remote attackers to bypass authentication on affected installations of PaperCut NG 22.0.5 (Build 63914). Authentication is not required to exploit this vulnerability. An attacker can leverage this vulnerability to bypass authentication and execute arbitrary code in the context of SYSTEM. It was found that BlueSky Ransomware and Tor2Mine miner malware has been abusing this vulnerability since December 2022.
The POC to exploit for the above vulnerability:
https://packetstormsecurity.com/files/172512/PaperCut-NG-MG-22.0.4-Remote-Code-Execution.html
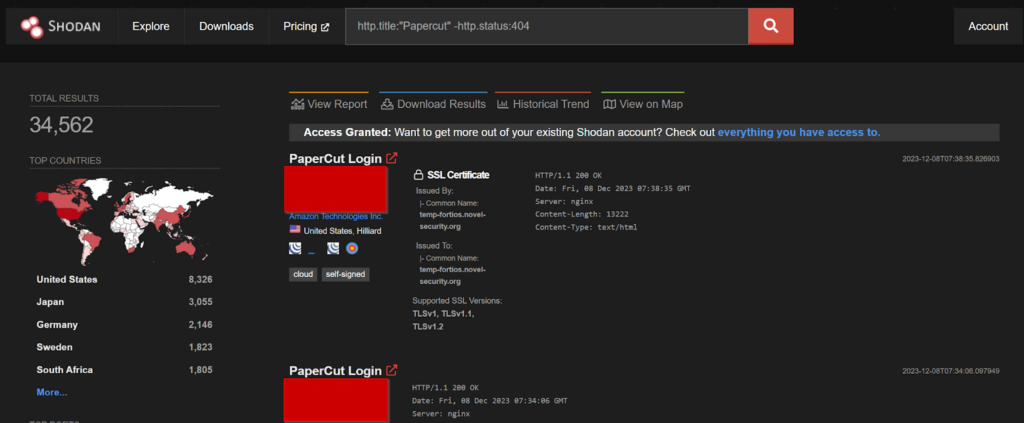
Nearly 35K endpoints currently accessible in shodan
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.