Critical CVEs: Fortinet, Oracle, PostgreSQL, WS_FTP Server and More
This week, from February 19th to 23rd, the FireCompass research team identified a huge number of CVEs that are high in severity, along with ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are in popular commercial products used by various industries, and there are also new and well-known malware- targeting industries. In this report, we will list important CVEs discovered as well as the list of malware, threat actors, and botnets that were most active, along with the CVEs they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2024-1708, CVE-2024-1709 – ConnectWise ScreenConnect Multiple Vulnerability
- CVE-2024-1474 – WS_FTP Server
- CVE-2023-42791 – Fortinet FortiManager
- CVE-2024-20917 – Oracle Enterprise Manager Base
- CVE-2024-20927, CVE-2024-20931 – Oracle WebLogic Server Multiple Vulnerability
- CVE-2024-20953 – Oracle Agile PLM
- CVE-2024-1597 – PostgreSQL JDBC Driver
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Detailed Analysis: Vulnerabilities
CVE-2024-1708, CVE-2024-1709 – ConnectWise ScreenConnect Multiple Vulnerability:
CVE-2024-1708
ConnectWise ScreenConnect versions 23.9.7 and earlier contain a critical path-traversal vulnerability (CVE-2024-1708), exposing systems to potential remote code execution, data breaches, and critical system interference. Attackers can exploit this vulnerability through crafted user interactions. It is imperative to update to the latest version (23.9.8) promptly. Though technical details and exploits are not publicly available, the severity demands immediate action to mitigate risks. If updating is not feasible in the short term, consider alternative products. Remember, early patching is crucial to safeguard your environment.
CVE-2024-1709
ConnectWise ScreenConnect versions 23.9.7 and earlier present a critical security risk due to CVE-2024-1709, an “Authentication Bypass Using an Alternate Path or Channel” vulnerability. This exposes systems to potential attackers gaining direct access to sensitive data and critical systems by bypassing regular authentication. While technical details and potential exploits haven’t been publicly disclosed yet, the severity demands immediate action. Swiftly update to the latest version (23.9.8) to mitigate the risk. If updating isn’t feasible in the short term, consider alternative products and implement additional security measures. Remember, early patching is crucial to protect your environment from unauthorized access and potential compromise.
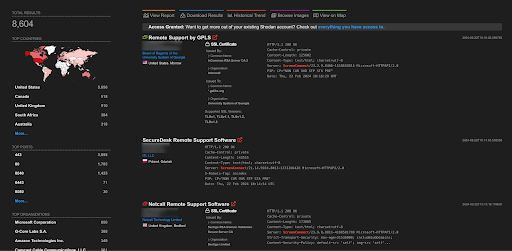
A total of more than 8K endpoints of ScreenConnect are exposed on the Shodan.
CVE-2024-1474 – WS_FTP Server
WS_FTP Server versions prior to 8.8.5 harbor a critical vulnerability (CVE-2024-1474) known as reflected cross-site scripting (XSS). This vulnerability enables attackers to inject malicious code into the administrative interface via user-supplied data, potentially leading to the theft of sensitive information, compromise of user accounts, or dissemination of malware. It is imperative to update to version 8.8.5 immediately to mitigate this high-risk vulnerability.
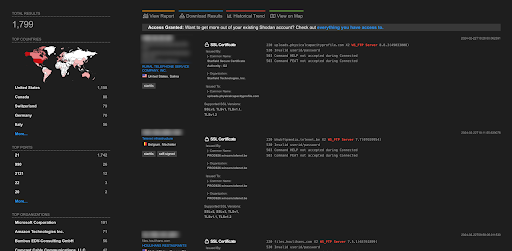
A total of more than 1.7K endpoints of WS_FTP Server are exposed on the Shodan.
CVE-2023-42791 – Fortinet FortiManager
CVE-2023-35188 exposes a critical security risk in SolarWinds Platform versions up to 2023.4.2. It allows attackers to remotely execute malicious code within the platform if they have valid user credentials. This vulnerability arises from a flaw in how the platform handles SQL statements, specifically within the “create” function. While user authentication is required for exploitation, attackers could potentially leverage stolen credentials or social engineering tactics to gain access. Upgrading to the latest SolarWinds Platform version (2023.4.3 or later) is essential to mitigate this risk.
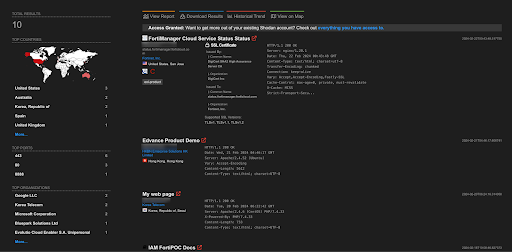
A total of 10 endpoints of Fortinet FortiManager are exposed on the Shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2024-20917 – Oracle Enterprise Manager Base
Oracle Enterprise Manager Base Platform version 13.5.0.0 contains a vulnerability (CVE-2024-20917) that, while challenging to exploit, permits unauthenticated attackers with network access to potentially gain unauthorized access to critical data, manipulate or delete some data, and even induce a partial service outage. Despite necessitating human interaction, successful attacks can profoundly impact other products beyond the platform itself. It is imperative to update to a patched version promptly to mitigate this high-risk vulnerability.
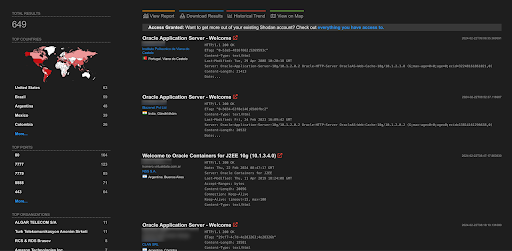
A total of 10 endpoints of Oracle Enterprise Manager are exposed on the Shodan.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
CVE-2024-20927, CVE-2024-20931 – Oracle WebLogic Server Multiple Vulnerability:
CVE-2024-20927
A critical vulnerability (CVE-2024-20927) impacts Oracle WebLogic Server versions 12.2.1.4.0 and 14.1.1.0.0, enabling unauthenticated attackers with network access to readily compromise the server and potentially access, modify, or delete critical data. Although the vulnerability is within the WebLogic Server, its exploitation can substantially affect other connected products. Take immediate action to update to a patched version to rectify this high-risk issue.
CVE-2024-20931
Oracle WebLogic Server versions 12.2.1.4.0 and 14.1.1.0.0 are susceptible to a critical vulnerability (CVE-2024-20931) that permits unauthenticated attackers with network access via T3 or IIOP protocols to compromise the server. This vulnerability, which is easily exploitable, grants attackers unauthorized access to potentially all critical data stored on the server. Due to the high risk of data breaches (CVSS score 7.5), it is imperative to update to a patched version immediately.
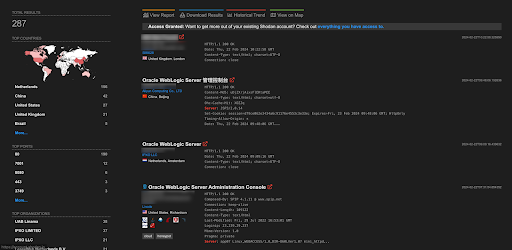
A total of 287 endpoints of Oracle WebLogic Server are exposed on the Shodan.
CVE-2024-20953 – Oracle Agile PLM
Oracle Agile PLM version 9.3.6 is vulnerable to a critical security flaw (CVE-2024-20953) that allows attackers with low privileges and network access via HTTP to completely take over the system. This easily exploitable vulnerability grants attackers unrestricted control over Oracle Agile PLM, potentially enabling them to steal, modify, or delete sensitive data. Update to a patched version immediately to address this high-risk vulnerability (CVSS score: 8.8).
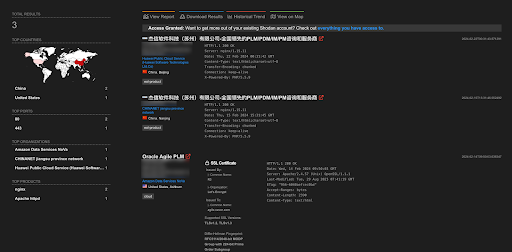
A total of 287 endpoints of Oracle Agile PLM are exposed on the Shodan.
CVE-2024-1597 – PostgreSQL JDBC Driver
PostgreSQL JDBC Driver (pgjdbc) versions before 42.7.2 contain a critical SQL injection vulnerability (CVE-2024-1597) if using the “PreferQueryMode=SIMPLE” setting, which is not the default. Attackers can exploit this by crafting specific input that bypasses protections and injects malicious SQL code, potentially compromising data or taking control of systems. Update to versions 42.7.2, 42.6.1, 42.5.5, 42.4.4, 42.3.9, or 42.2.8 immediately, or disable “PreferQueryMode=SIMPLE” if updating is not feasible. Remember, default settings are often more secure, and staying updated is crucial for maintaining security.
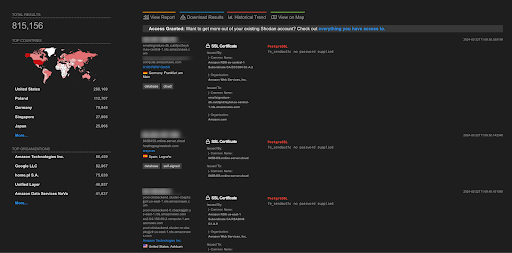
A total of more than 815K endpoints of PostgreSQL are exposed on the Shodan.
Blog By
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.